Picked up some cameras, now time to work on the network. I will be purchasing a new router and am looking for advice on the right model. I'm looking to support VPN and also VLANs to segregate my cameras from the rest of the network. I would like to be able to use a UI and not have to use a CLI for setup and monitoring. From all of the sound advice on this forum, it sounds like Asus is the way to go for my experience level, but I'm not sure if they support VLANs for example the AC1900 listed in the CliffNotes on the Wiki makes no mention of VLAN capabilities in the user manual. Searching for other VLAN setup on other Asus routers show similar results. Would I need to flash the router with a different system to be able to have it support VLANs? New to networking setup so any advice to learn more about VLANs would also be much appreciated. So whats your recommendation for a NOOB friendly OpenVPN supporting, VLAN capable, UI accessible router? Thanks!
Looking for a NOOB friendly OpenVPN VLAN supported router
- Thread starter Poe Cameraon
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
SouthernYankee
IPCT Contributor
All New ASUS routers support OpenVPN. I have an old RT-AC66U_B1, it works great. The main difference in ASUS routers is the WIFI support.
Setting up OpenVPN on an ASUS router is very simple.
I do not us a VLAN. I use Blue Iris with a separate NIC to physically separate the cameras from my home network.
Setting up OpenVPN on an ASUS router is very simple.
I do not us a VLAN. I use Blue Iris with a separate NIC to physically separate the cameras from my home network.
Thanks @SouthernYankee, I'll take a look at that as an option. I like the idea of physically separating the two networks so less chance of access. So instead of the first topology below I would need the second...complicates things as I was hoping to not have to run any additional lines to my garage.
Single NIC
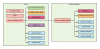
Separate BlueIris NIC
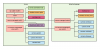
I think it may be good to have VLAN support for some other uses as well. I'm still trying to learn the interplay of the router or the managed switch in VLAN setup. Anyone have any good primers to share? I would prefer an unmanged switch if I can setup VLANs just through the router but am unclear if that is possible or if it needs to be managed via the switch.
Single NIC
Separate BlueIris NIC
I think it may be good to have VLAN support for some other uses as well. I'm still trying to learn the interplay of the router or the managed switch in VLAN setup. Anyone have any good primers to share? I would prefer an unmanged switch if I can setup VLANs just through the router but am unclear if that is possible or if it needs to be managed via the switch.
SouthernYankee
IPCT Contributor
excellence diagrams.
The reason for the two NIC approach is that from a technology it is simple to implement and very easy to understand. Running the wires is a PIA.
The reason for the two NIC approach is that from a technology it is simple to implement and very easy to understand. Running the wires is a PIA.
Q™
IPCT Contributor
Asus RT-AC68U! I have seven and they're (7) all good. Caution get the RT-AC68U model and not the T-Mobile units which are often advertised incorrectly as the RT-AC68U...they're not. Also, I've had trouble uploading firmware to the RT-AC68R. When purchasing the RT-AC68U, try to get a unit with a "hardware revision" greater than "A1".
SG-1100 is good. I was debating on that one but went Ubiquiti EdgeRouterX instead cus it was cheaper. Both will be able to do what you need to do.
Thanks for the input all. So my plan is to get a SG-1100 router/firewall running pfSense. I will be adding an additional NIC to my Blue Iris PC and have one NIC connected to the camera LAN and the other connected to my secured LAN. On the secured LAN side I will be getting a Ubiquiti UniFi POE Switch for VLAN setup for the rest of my network.
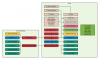

New and learning. What is the purpose of separating the cameras from the main network? ...security access from outside? If that why not just set up access control on the router to prevent the camera IP from contacting the WAN? Which is what I did, or does that not work. Even if your cameras are behind the BI computer, can't someone still get to them...they are technically still on the same network aren't they?
Hammerhead786
Pulling my weight
- Apr 23, 2018
- 248
- 165
New and learning. What is the purpose of separating the cameras from the main network? ...security access from outside? If that why not just set up access control on the router to prevent the camera IP from contacting the WAN? Which is what I did, or does that not work. Even if your cameras are behind the BI computer, can't someone still get to them...they are technically still on the same network aren't they?
If you currently have an Asus router you could install FreshTomato firmware which would give you vlan capability. Cameras can be easily hacked. You would not want a compromised camera on the same network as your main network. If you have blocked your cameras at the router from contacting the internet, then in all likelihood you are good.
My personal preference is to have the cameras on one vlan and the BI machine on a separate vlan using a managed layer 3 switch. I can then configure the vlan for the cameras to only pass traffic to the BI machine. I have the BI machine connected to my router and therefore it has internet access for software updates and time synchronisation.
If I need to access the cameras directly, I RDP into the BI machine and access them from there. I can also do this externally using a VPN. Some might say this is overly complicated when I could use a PC with dual NICs, but for me it works and provides me with a great level of flexibility.
SouthernYankee
IPCT Contributor
NO NO. The cameras are on a separate network not connected to the internet so there is zero access for the cameras to the internet. The cameras can call home. With the way networking works and the current state of software passwords and access control is nearly useless.
If you try to block a device at the router by either an IP address or a MAC address, the device will just change its address and by pass the block. Physical separation is the only way to go.
If you try to block a device at the router by either an IP address or a MAC address, the device will just change its address and by pass the block. Physical separation is the only way to go.
The Automation Guy
Known around here
If you try to block a device at the router by either an IP address or a MAC address, the device will just change its address and by pass the block. Physical separation is the only way to go.
No argument that physical separation is the BEST way to go, but it is a stretch to say it is the the only way to go.......
and I've never seen a device that when set to a static network address (either locally or by a static DHCP rule on the router), automatically update it's address because it couldn't access the internet......
SouthernYankee
IPCT Contributor
I have seen a number of device change there mac an static IP address. I have seen no name cameras do it. I have seen hacked network equipment do it. I have seen refurbished equipment do it, like printers I use to work in a top 10 S&P company in software engineering. The company does not even let any outside devices use there local network. No personal cell phones or tablets on wifi. All devices must go through in house test and certification. NO USBs are allowed as the micro code in them is hacked.
Last edited:
If you login via SSH and delete the .tar.gz file of T-Mobile security certificates from mtd5, it's exactly the same as an RT-AC68/U.Asus RT-AC68U! I have seven and they're (7) all good. Caution get the RT-AC68U model and not the T-Mobile units which are often advertised incorrectly as the RT-AC68U...they're not. Also, I've had trouble uploading firmware to the RT-AC68R. When purchasing the RT-AC68U, try to get a unit with a "hardware revision" greater than "A1".
Many Chinese firmwares will use hard-coded DNS server IP addresses when they cannot get out to the internet. You would not believe some of the things they do.No argument that physical separation is the BEST way to go, but it is a stretch to say it is the the only way to go.......
and I've never seen a device that when set to a static network address (either locally or by a static DHCP rule on the router), automatically update it's address because it couldn't access the internet......
What is the headless audio player in your system?Thanks for the input all. So my plan is to get a SG-1100 router/firewall running pfSense. I will be adding an additional NIC to my Blue Iris PC and have one NIC connected to the camera LAN and the other connected to my secured LAN. On the secured LAN side I will be getting a Ubiquiti UniFi POE Switch for VLAN setup for the rest of my network.
View attachment 50466
