My issue is there still after swap, beginning to think its defective or the wiring in the house is not wired properly as I tried to get a reading of the transformer and the multimeter is not showing the right numbersCurrently I have the one that came with the house which is a NuTone 515-t and its' a 10v 5w transformer. So it might be that it's not giving enough power to the unit.
I have just purchased a brand new chime a couple months ago so it should handle higher voltages.
I can also confirm that I flashed the firmware with the original EZVIZ and it still was offline this morning. Will upgrade the transformer and check to see if it keeps happening.
New RCA HSDB2A 3MP Doorbell IP Camera
- Thread starter fleece
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
MicahJames
Pulling my weight
Hi all.
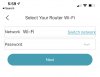
Having trouble re-adding my RCA doorbell with the app. Everything seemed normal but when I go to select WiFi it just says “WiFi” I assume that means it’s taking the name of the WiFi I’m currently on.
After proceeding, the bell says it is not an ideal WiFi environment and may impact performance. It ultimately fails in the app and makes me restart the whole process.
Any idea appreciated.
Having trouble re-adding my RCA doorbell with the app. Everything seemed normal but when I go to select WiFi it just says “WiFi” I assume that means it’s taking the name of the WiFi I’m currently on.
After proceeding, the bell says it is not an ideal WiFi environment and may impact performance. It ultimately fails in the app and makes me restart the whole process.
Any idea appreciated.
Attachments
MicahJames
Pulling my weight
msmcknight
n3wb
Guys, I'm lost. In an act of desperation I connected the hik-connect app. In the hopes of finding a configuration option that I cant find in iVMS or ONVIF (ie. chime type). Within hik-connect app, I can't find any place where the camera settings are located. I can see setting options for the hik-connect app itself, and the camera's network/wifi setting. I can get a live view, but nowhere do I see anything about storage, image quality, overlay settings... nothing about configuring the camera itself.
What am I missing?!??? Grrrrr!!!!!
Thanks!
What am I missing?!??? Grrrrr!!!!!
Thanks!
msmcknight
n3wb
Well guys, I finally got this thing working. Here's what I've learned...
I had configured the whole thing and had it up and running with iVMS and BI... everything except the chime... without using the hikconnect app at all. Unfortunately, there is no way to configure it to use a chime without using the app. The doorbell defaults to "no chime" -- which explains why I wasn't seeing any voltage change when the button was pressed.
From a security standpoint, this thing is a mess. First of all, having to use the app has it's own problems...
It turns out this thing just assumes you're on an insecure network and allow any kind of outbound traffic out by default. I'm sure this is true for the vast amount of non-technical consumers out there, but it doesn't play nice on a secured network at all. This was the biggest problem I was running into and didn't realize it until I started digging into traffic patterns. When I would set up the phone, using the app like a good boy, it would tell me "wifi configured" and I could see it show up on my network. I could ping it and even get a live view from it... but the app would eventually time-out and complain that the network configuration failed. That's weird... it literally just spoke to me and said it had succeeded! Grrrr!!!!!!
Lot's of "interesting" network traffic was being blocked by my firewall. Most internet based products make use of well known ports like 80 and 443 and are happy with those. Not hikvision... they want ports 123, 8800, 31006, 8666, ICMP, 6002, 6500, and 5228...
The camera itself reaches out to:
123 (NTP) - first hitting a server in China (time.ys7.com). After configuration is complete, this changes to 0.amazon.pool.ntp.org.
8800 - amazon hosted server
31006 - amazon hosted server
8666 - amazon hosted server
ICMP - pings it's gateway every 30 seconds.
6002 - an unresolvable server in Singapore.
5228 - google hosted server
6500 - amazon hosted server
The hik-connect app reaches out to:
8666, 8800 and 6500
Of all those ports it tried to use, I only allowed 123, 8800, 31600, 8666, and ICMP. Once I did that, I was able to get the app to configure the camera... including the option to set my chime type. Finally!
When I did all of this, I spun-up a "test" access point and connected the camera and my tablet to it. I did not want to connect them to my true internal network given the blatant security problems with the entire product/app combo. Once I had the camera configured and was ready to move it to my "real" network, I connected my laptop to the test network and connected to the camera via iVMS so I could change the wifi settings and admin password and not have to worry about the hikconnect app passing those details to who knows where. Once on my real network, I have my DHCP server set to not give the camera any DNS servers and it points it's gateway at another internal host so it can ping (otherwise it will drop the wifi every 5 minutes).
Unfortunately, hikvision made this camera a nightmare to deal with. Every bit of this hassle could have been avoided if they had just allowed the setting of the chime via the normal ONVIF and iVMS protocols. There were a few others also only available from the app... microphone control and indicator light on/off come to mind. Why on earth would they leave these out of the standard configuration protocols??!?!?!? Geez.
I'm sure it all goes swell for folks who aren't as privacy concious, or aren't technical enough to worry about the traffic on their network, but if you're at all security conscious and were hoping to get a self-contained offline camera for your doorbell, this isn't it.
As for compatibility with iVMS... which it clearly claims it has on the product datasheet... it's missing a few key components...
I had configured the whole thing and had it up and running with iVMS and BI... everything except the chime... without using the hikconnect app at all. Unfortunately, there is no way to configure it to use a chime without using the app. The doorbell defaults to "no chime" -- which explains why I wasn't seeing any voltage change when the button was pressed.
From a security standpoint, this thing is a mess. First of all, having to use the app has it's own problems...
- It requires location services to be enabled and it must have permission to them or it will refuse to continue. There is no justifiable reason for this requirement.
- It requires access to photos, storage and other stuff that it also shouldn't need to have.
- It automatically takes the wifi settings (SSID & Password) from your phone/tablet and feeds them to the camera.
It turns out this thing just assumes you're on an insecure network and allow any kind of outbound traffic out by default. I'm sure this is true for the vast amount of non-technical consumers out there, but it doesn't play nice on a secured network at all. This was the biggest problem I was running into and didn't realize it until I started digging into traffic patterns. When I would set up the phone, using the app like a good boy, it would tell me "wifi configured" and I could see it show up on my network. I could ping it and even get a live view from it... but the app would eventually time-out and complain that the network configuration failed. That's weird... it literally just spoke to me and said it had succeeded! Grrrr!!!!!!
Lot's of "interesting" network traffic was being blocked by my firewall. Most internet based products make use of well known ports like 80 and 443 and are happy with those. Not hikvision... they want ports 123, 8800, 31006, 8666, ICMP, 6002, 6500, and 5228...
The camera itself reaches out to:
123 (NTP) - first hitting a server in China (time.ys7.com). After configuration is complete, this changes to 0.amazon.pool.ntp.org.
8800 - amazon hosted server
31006 - amazon hosted server
8666 - amazon hosted server
ICMP - pings it's gateway every 30 seconds.
6002 - an unresolvable server in Singapore.
5228 - google hosted server
6500 - amazon hosted server
The hik-connect app reaches out to:
8666, 8800 and 6500
Of all those ports it tried to use, I only allowed 123, 8800, 31600, 8666, and ICMP. Once I did that, I was able to get the app to configure the camera... including the option to set my chime type. Finally!
When I did all of this, I spun-up a "test" access point and connected the camera and my tablet to it. I did not want to connect them to my true internal network given the blatant security problems with the entire product/app combo. Once I had the camera configured and was ready to move it to my "real" network, I connected my laptop to the test network and connected to the camera via iVMS so I could change the wifi settings and admin password and not have to worry about the hikconnect app passing those details to who knows where. Once on my real network, I have my DHCP server set to not give the camera any DNS servers and it points it's gateway at another internal host so it can ping (otherwise it will drop the wifi every 5 minutes).
Unfortunately, hikvision made this camera a nightmare to deal with. Every bit of this hassle could have been avoided if they had just allowed the setting of the chime via the normal ONVIF and iVMS protocols. There were a few others also only available from the app... microphone control and indicator light on/off come to mind. Why on earth would they leave these out of the standard configuration protocols??!?!?!? Geez.
I'm sure it all goes swell for folks who aren't as privacy concious, or aren't technical enough to worry about the traffic on their network, but if you're at all security conscious and were hoping to get a self-contained offline camera for your doorbell, this isn't it.
As for compatibility with iVMS... which it clearly claims it has on the product datasheet... it's missing a few key components...
- It will not send motion events to iVMS. It will send PIR events, but not motion detection events.
- It does not support a privacy mask.
- It does not support the storage server, meaning it can only record to it's internal SD card.
- There are probably more I just haven't stumbled across yet.
That’s nowhere near enough power.
I can report that I have installed a new transformer on Saturday evening and it has been working since. Thanks everyone for the help!
The SD-Card records PIR Events unless you change the Event settings in iVMS-4200 or Batch Config. Tool. I have had the same SD-Card for a year and a half at default settings, if this helps...I can't really comment on lifespan of SD-Cards...For recording what settings/ bitrate/ frame rate do you guys recommend to extend the lifespan of the microSD card?
I know Pete here is a Zoneminder guy...New DS-HD1 owner here. Have read the 101 and looking for more detail on setting config options. For cameras that try to phone home I have disconnected internet and then connected the camera, then set IP by MAC on the router and disable WAN access so the camera never has internet access. (you're not paranoid if they really are after you.). Since I need to set this up via wireless it will have to be a little different. I could use the ap on my android or install the batch configuration tool or IVMS4200. Is there a table or details somewhere that shows what settings can be controlled with each? I may give cloud access at some point but for now I planned to just use it with zoneminder. Would be good if I could trigger a script on the zoneminder box when the button is pressed - what functionality is possible on button press without internet access and the app? I have seen the details on current sensors and fully understand that option but was looking for what might be done with just settings and software.
I am sorry the trans. did not fix your issue. I know we had one guy who had a bad wire that caused intermittent issues. But for it to hose like that it does sound more like a faulty Doorbell, I would call EZVIZ Support and see what they suggest. You have a year warranty with them.I have swapped my transformer and it is 16v 30va and I am still getting the issue "too many viewers, failed to play" and when thus happens, the chime does not work as well. Seems like no one else has this problem so I'm not sure if the product is defective or not
Thank you for your write-up, will include a link in our 101...Well guys, I finally got this thing working. Here's what I've learned...
I had configured the whole thing and had it up and running with iVMS and BI... everything except the chime... without using the hikconnect app at all. Unfortunately, there is no way to configure it to use a chime without using the app. The doorbell defaults to "no chime" -- which explains why I wasn't seeing any voltage change when the button was pressed.
From a security standpoint, this thing is a mess. First of all, having to use the app has it's own problems...
So, you basically have an app requiring location data and has access to your wifi SSID and password... with those three things, someone could locate your home and gain access to your network with little to no effort. On top of that, it's communicating to at least two servers in Asia as soon as it comes online, as well as several amazon hosted servers. There's a decent chance this sensitive data is making it's way to one of those servers.
- It requires location services to be enabled and it must have permission to them or it will refuse to continue. There is no justifiable reason for this requirement.
- It requires access to photos, storage and other stuff that it also shouldn't need to have.
- It automatically takes the wifi settings (SSID & Password) from your phone/tablet and feeds them to the camera.
It turns out this thing just assumes you're on an insecure network and allow any kind of outbound traffic out by default. I'm sure this is true for the vast amount of non-technical consumers out there, but it doesn't play nice on a secured network at all. This was the biggest problem I was running into and didn't realize it until I started digging into traffic patterns. When I would set up the phone, using the app like a good boy, it would tell me "wifi configured" and I could see it show up on my network. I could ping it and even get a live view from it... but the app would eventually time-out and complain that the network configuration failed. That's weird... it literally just spoke to me and said it had succeeded! Grrrr!!!!!!
Lot's of "interesting" network traffic was being blocked by my firewall. Most internet based products make use of well known ports like 80 and 443 and are happy with those. Not hikvision... they want ports 123, 8800, 31006, 8666, ICMP, 6002, 6500, and 5228...
The camera itself reaches out to:
123 (NTP) - first hitting a server in China (time.ys7.com). After configuration is complete, this changes to 0.amazon.pool.ntp.org.
8800 - amazon hosted server
31006 - amazon hosted server
8666 - amazon hosted server
ICMP - pings it's gateway every 30 seconds.
6002 - an unresolvable server in Singapore.
5228 - google hosted server
6500 - amazon hosted server
The hik-connect app reaches out to:
8666, 8800 and 6500
Of all those ports it tried to use, I only allowed 123, 8800, 31600, 8666, and ICMP. Once I did that, I was able to get the app to configure the camera... including the option to set my chime type. Finally!
When I did all of this, I spun-up a "test" access point and connected the camera and my tablet to it. I did not want to connect them to my true internal network given the blatant security problems with the entire product/app combo. Once I had the camera configured and was ready to move it to my "real" network, I connected my laptop to the test network and connected to the camera via iVMS so I could change the wifi settings and admin password and not have to worry about the hikconnect app passing those details to who knows where. Once on my real network, I have my DHCP server set to not give the camera any DNS servers and it points it's gateway at another internal host so it can ping (otherwise it will drop the wifi every 5 minutes).
Unfortunately, hikvision made this camera a nightmare to deal with. Every bit of this hassle could have been avoided if they had just allowed the setting of the chime via the normal ONVIF and iVMS protocols. There were a few others also only available from the app... microphone control and indicator light on/off come to mind. Why on earth would they leave these out of the standard configuration protocols??!?!?!? Geez.
I'm sure it all goes swell for folks who aren't as privacy concious, or aren't technical enough to worry about the traffic on their network, but if you're at all security conscious and were hoping to get a self-contained offline camera for your doorbell, this isn't it.
As for compatibility with iVMS... which it clearly claims it has on the product datasheet... it's missing a few key components...
Some of these can be overcome by using blue iris instead of iVMS, but when you have 16 other cameras that are all hikvision and you've built infrastructure designed around their solutions, adding this one camera really shouldn't kink up the works as bad as it does. They just half-assed this one and from a company that generally produces excellent products, it has been disappointing.
- It will not send motion events to iVMS. It will send PIR events, but not motion detection events.
- It does not support a privacy mask.
- It does not support the storage server, meaning it can only record to it's internal SD card.
- There are probably more I just haven't stumbled across yet.
It is strange that it does not work on Hik's Storage Server...
The SD-Card records PIR Events unless you change the Event settings in iVMS-4200 or Batch Config. Tool. I have had the same SD-Card for a year and a half at default settings, if this helps...I can't really comment on lifespan of SD-Cards...
Could you post what the default settings are? I made changes by mistake and I forgot what the original settings were. My SD card died after 3 months. I was using a non endurance card. I bought a new card now which is high endurance. Hopefully, that lasts longer.
So this is just scheduling defaults (Alarm Template):Could you post what the default settings are? I made changes by mistake and I forgot what the original settings were. My SD card died after 3 months. I was using a non endurance card. I bought a new card now which is high endurance. Hopefully, that lasts longer.
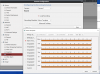
When I said default, I just meant I did not change anything. If you used Custom and changed/used one of the tabs, Continuous/Event/Command/Other then to get back to default just chose Alarm Template. Hopefully we are on the same page, not sure what you changed...
So this is just scheduling defaults (Alarm Template):
View attachment 80539
When I said default, I just meant I did not change anything. If you used Custom and changed/used one of the tabs, Continuous/Event/Command/Other then to get back to default just chose Alarm Template. Hopefully we are on the same page, not sure what you changed...
Here's what I changed, I am wondering if there's anything I need to adjust...

So not sure where that screen is from, but since it is Main Stream that is your RTSP settings for recording to a NAS. NVR, Blue Iris, etc. Those settings should not effect your SD-Card. I think going with a better card should solve your short lifespan issue. I bought a SD-Card that was V30 rated, meaning a card that can handle video recording...Here's what I changed, I am wondering if there's anything I need to adjust...

Here are my RSTP settings that records on Blue Iris (They are not default settings):
Full Frame = 30FPS (15FPS is default)
Think I also changed to Highest Video Quality too
Don't remember changing Bit Rate so it may be default.
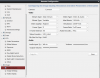
The SD-Card I have:
HTH
EDIT: I would say I am wrong, actually some of those settings may effect your SD-Card recordings, I truly do not know, I know you can download your recordings from your SD-Card via iVMS-4200 or Batch Config. Tool. From there you can load in VLC and see what Res. they save as.
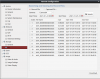
EDIT2: Ok, oh yeah I am wrong, sorry it has been over a year since I played with my SD-Card recordings. I downloaded the first recording on the above list and I see it recorded at 30 FPS (which is not default FPS), here is my Codec info from VLC:

With Blue Iris, I really have no reason to go to the SD-Card for recordings, it is nice that it is a backup though, incase my BI Box stops...Also what is nice is the recordings are saved in MP4 format...
Last edited:
msmcknight
n3wb
It is strange that it does not work on Hik's Storage Server...
Yeah, that was a bummer. It took 2 phone calls and 4 emails with Hik-Vision to finally get them to reveal that it wasn't compatible with the storage server. Whats so aggrivating about it is that it's actually sending the data to the storage server. tcpdump shows a constant stream from the camera. My guess that there's something with event-triggering that's not working so the storage server never gets told to record. I tried full-time recording and still couldn't get it to work. Ugh!
So I know nothing about Hik's Storage Server but can it except feeds from other sources or only Hik Cams? Just thinking like VLC, Monocle, tinyCam Pro, Blue Iris Servers, etc. and maybe direct the feed to Hik's?Yeah, that was a bummer. It took 2 phone calls and 4 emails with Hik-Vision to finally get them to reveal that it wasn't compatible with the storage server. Whats so aggrivating about it is that it's actually sending the data to the storage server. tcpdump shows a constant stream from the camera. My guess that there's something with event-triggering that's not working so the storage server never gets told to record. I tried full-time recording and still couldn't get it to work. Ugh!
I can't get BI to successfully do motion detection on this device. The RCA PIR notification on my phone works, but not BI. I can review the footage and toggle "test run video through motion detector" and it highlights the motion as expected but it didn't trigger when it originally was recorded.
I have the motion detection set very liberally (I'll pass the results to AI to help filter alerts). My min object size is 200, min contrast is 20, min duration is 0.5s. I'm using edge vector algorithm. Maybe a different algo will work better?
Any tips on how different settings I can try? Doesn't seem like a device issue to me but my other cameras seem to be working fine.
I have the motion detection set very liberally (I'll pass the results to AI to help filter alerts). My min object size is 200, min contrast is 20, min duration is 0.5s. I'm using edge vector algorithm. Maybe a different algo will work better?
Any tips on how different settings I can try? Doesn't seem like a device issue to me but my other cameras seem to be working fine.
msmcknight
n3wb
So I know nothing about Hik's Storage Server but can it except feeds from other sources or only Hik Cams? Just thinking like VLC, Monocle, tinyCam Pro, Blue Iris Servers, etc. and maybe direct the feed to Hik's?
Not that I know of. I think it's probably proprietary to hikvisions cameras so it probably works for most cameras they white-label that also work with iVMS... for now. I just heard from hikvision earlier today that they were discontinuing the storage server at the end of this month... I have no idea what their plan is to replace that functionality. I've asked for some details and will pass on if they share anything more about it.
MicahJames
Pulling my weight
I’ve never been able to get BI to do motion alerts on my RCA doorbell. I gave up and just use the app nowI can't get BI to successfully do motion detection on this device. The RCA PIR notification on my phone works, but not BI. I can review the footage and toggle "test run video through motion detector" and it highlights the motion as expected but it didn't trigger when it originally was recorded.
I have the motion detection set very liberally (I'll pass the results to AI to help filter alerts). My min object size is 200, min contrast is 20, min duration is 0.5s. I'm using edge vector algorithm. Maybe a different algo will work better?
Any tips on how different settings I can try? Doesn't seem like a device issue to me but my other cameras seem to be working fine.
msmcknight
n3wb
A little more scariness on this camera. Let's say you enter remote configuration via iVMS or BI and change the admin password... you don't do it through their app... well, their app still has access to the camera, even though it has no knowledge of the new password you set. If you change the password within the app, they store it so they can continue to gain access to the camera. So, as long as the camera is connected to the internet... with or without the app... they have admin access to the camera. And, given this access, they might even be able to read what the current password is. My 0.02 worth... keep this camera (and it's clones) isolated from the internet.
PS. I heard back from Hikvision about the storage server. Looks like they are discontinuing it along with the Stream Server. They are pushing those functions to only their professional product (HikCentral Professional) which costs... a lot... I mean a LOT... if you have more than 8 cameras. For now, I'm guessing the existing storage server will continue to work for the bulk of their cameras, but at some point down the road, iVMS's usability will fade. I guess Hikvision wants out of the consumer space.
PS. I heard back from Hikvision about the storage server. Looks like they are discontinuing it along with the Stream Server. They are pushing those functions to only their professional product (HikCentral Professional) which costs... a lot... I mean a LOT... if you have more than 8 cameras. For now, I'm guessing the existing storage server will continue to work for the bulk of their cameras, but at some point down the road, iVMS's usability will fade. I guess Hikvision wants out of the consumer space.