Hello,
I DID RECOVER MY MIN-SYSTEM!

As I've seen in the mtd8 images that there were a lot of spare space at the end of the partition and as the bad block in my cam was at the begining of the partition I first decided to relocate the useful data after the bad block and to boot manually to the good offset from uboot when needed.
Here are the steps I wanted to do:
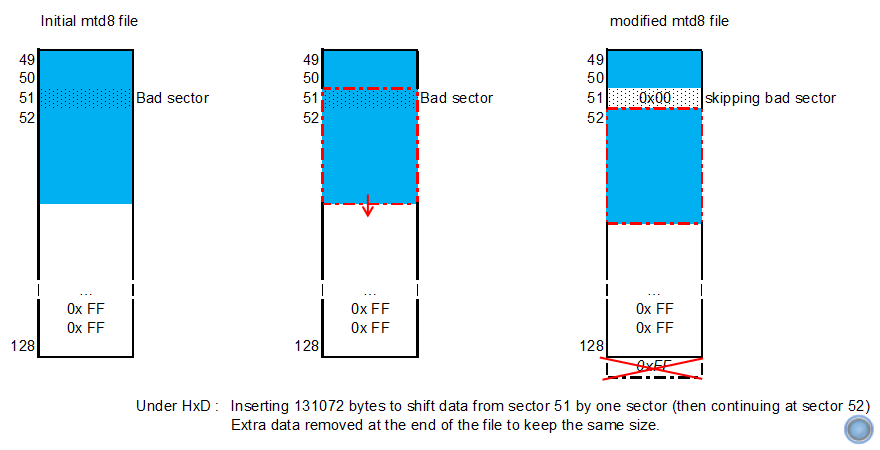
1) Creating the new file by inserting spare data (multiple of block size) at the begining of the file using HxD and deleting spare data at the end to keep the size of the file unchanged.
2) Find the mapping of the NAND from the u-boot point of view to be able to jump at the right offset (using "bootm" maybe)?
I didn't know how to get the NAND mapping in u-boot so I've played with "help" under u-boot and found the useful "show flash" command:
Code:
HKVS # show flash
RCT configured to NAND mode
main size: 2048
pages per block: 64
bst partition blocks: 0 - 1
ptb partition blocks: 1 - 9
bld partition blocks: 9 - 17
hal partition blocks: 17 - 25
ano_ptb partition blocks: 25 - 33
env partition blocks: 33 - 37
param partition blocks: 37 - 41
dpt partition blocks: 41 - 49
rcvy partition blocks: 49 - 129
krn_pri partition blocks: 129 - 193
krn_sec partition blocks: 193 - 257
rmd_pri partition blocks: 257 - 289
rmd_sec partition blocks: 289 - 321
app_pri partition blocks: 321 - 513
app_sec partition blocks: 513 - 705
cfg_pri partition blocks: 705 - 737
cfg_sec partition blocks: 737 - 769
dbg partition blocks: 769 - 897
With this command I found that the recovery partition was lying from blocks 49 to 128 which is confirmed by:
Code:
HKVS # show meta
bst sblk: 0 nblk: 1 on: NAND
ptb sblk: 1 nblk: 8 on: NAND
bld sblk: 9 nblk: 8 on: NAND
hal sblk: 17 nblk: 8 on: NAND
ano_ptb sblk: 25 nblk: 8 on: NAND
env sblk: 33 nblk: 4 on: NAND
param sblk: 37 nblk: 4 on: NAND
dpt sblk: 41 nblk: 8 on: NAND
rcvy sblk: 49 nblk: 80 on: NAND
krn_pri sblk: 129 nblk: 64 on: NAND
krn_sec sblk: 193 nblk: 64 on: NAND
rmd_pri sblk: 257 nblk: 32 on: NAND
rmd_sec sblk: 289 nblk: 32 on: NAND
app_pri sblk: 321 nblk: 192 on: NAND
app_sec sblk: 513 nblk: 192 on: NAND
cfg_pri sblk: 705 nblk: 32 on: NAND
cfg_sec sblk: 737 nblk: 32 on: NAND
dbg sblk: 769 nblk: 128 on: NAND
sblk: 0 nblk: 0 on: DEFAULT
sblk: 0 nblk: 0 on: DEFAULT
sm_stg[0] sblk: 0 nblk: 0
sm_stg[1] sblk: 0 nblk: 0
model name:
crc32: 0x9d57e812
But I still didn't know the base address of the NAND...
It doesn't matter because the "nandread" command allows to read data from a block and to write it into the DDR:
Code:
HKVS # help nandread
Help for 'nandread':
Usage: nand_read [ddr_addr] [block] [size]
read data from nand flash to ddr
need ddr address, start block in nand, data size
As I know that the "loadaddr" parameter shall point into the DDR I can read data from NAND to 0xc2000000 then use "dump" to show its contents
Code:
Usage: HKVS # help dump
Help for 'dump':
Usage: dump [8|16|32] [start address] - [end address]
Dump memory content in either 8-bit, 16-bit, or 32-bit mode
from specified starting and ending addresses
So let's verify that we can access the data from the recovery partition!
Code:
HKVS # nandread 0xc2000000 49 2048
done!
HKVS # dump 32 0xc2000000
0xc2000000 d3 f0 21 e3
Yes! This is the data at offset 0 of the mtd8 partition (compared with the reference file under HxD). So let's find the data at the begining of the bad sector that is located at offset 0x40000 as I can see in HxD:
Code:
HKVS # nandread 0xc2000000 51 2048
done!
HKVS # dump 32 0xc2000000
0xc2000000 5d 07 48 bd
Hey! It doesn't match the data I can read at offset 0x40000 (2 sectors x 64 pages x 2048 bytes) in HxD!... But it matches the data located at offset 0x60000 (next good sector)!.....
Would it be possible that u-boot knows where are located the bad sectors and skips them? Yes! Which is confirmed by the following command:
Code:
HKVS # show bbt
Bad block found at 29
Bad block found at 51
Bad block found at 966
I beleive that I could have write the min-system from u-boot but as I didn't know how to do so I'd rather modified my mtd8 file under HxD by inserting 0x20000 dummy data at offset 0x40000 and deleting 0x20000 spare data at the end of the file to keep the same size.
Then I've launched the boot with the "init=/bin/sh" option as described in a previous post to be able to populate the mtd8 partition with the modified image:
Code:
# cat mtd8_skip_block51 > /dev/mtdblock8
Finally I still don't know the base address of the NAND flash from u-boot but my min-system is fully fonctional now!

I've tried the Hikvision
TFTP update mode and it works!!!