user8963
Known around here
Andy told me there is no recourse for bricking them.
I dont think @EMPIRETECANDY is right... someone here in forum posted a link to a german forum where the recovery process is descirbed... maybe give it a try...
i am not sure why they change the firmware with hex edit... i would start with the 4.5 firmware and try to flash it with jounin tftpd (instead of cisco, never heard about that) ... if that fails... maybe you need to edit the firmware with hex edit
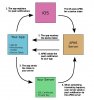
Here are the pictures where the TTL connector is (and pinout)
Code:
https://translate.google.com/translate?sl=auto&tl=en&u=https://www.ip-phone-forum.de/threads/vto-vth-tftp-ttl-anschlussbilder-sammlung.305575/Here is the tutorial
Code:
https://translate.google.com/translate?sl=auto&tl=en&u=https://www.ip-phone-forum.de/threads/vto2000a-c-nach-fw-update-nicht-mehr-erreichbar.304909/post-2346656Here is a collection of firmwares (if new one fail with tftpd)
[FAQ] - Dahua VTO/VTH Firmware Link-Sammlung / Anleitungen
Hab mir gedacht, um die immer gleichen Fragen bzgl. aktueller FW für die VTO's und VTH's im Keim zu ersticken, mach ich mal eine Linksammlung dafür. Jeder ist gerne dazu eingeladen mitzuarbeiten, aktuellere Versionen zu posten oder mir per PM zukommen zu lassen, ich werde diese dann hier...
Last edited: