Added VTO to the app
Which method did you use to add the VTO ?
SN/QR code, or IP address/domain ?
Added VTO to the app
IPWhich method did you use to add the VTO ?
SN/QR code, or IP address/domain ?
it is possible that this could be considered advanced networking since it involves firewall rules.Ok, so if 37777 isn't port forwarded to your VTO, I'm not sure how this works at all
it is possible that this could be considered advanced networking since it involves firewall rules.
37777 is not port forwarded. Port 37777 is open but only to my VPN (I have to add the reserved static IP of my smartphone as a 2nd IP). Maybe your 'port forward' definition is different from mine. Through my firewall, I have "ALLOWED" port 37777 to talk to my VPN gateway.
I'll explain more when I get home. But remember I am also using the UDM radius VPN server as well. So yes my VTO is by default on my camera network which is totally blocked other than NTP server. The VTO has allow rules to talk to Google IPs and specific Google ports. The BTO has to talk to Google solely and only for sending notification purposes. For the actual audio video purposes that remains inside my local networks through VPN.While manufacturers do sometimes use differing terminology, I use a UDM as well, and also have a selection of custom firewall rules, so we should be speaking the same language !
I'd be keen to work out what you're doing to make this work, as it would be good to avoid using the Dahua cloud if possible
- My VTO (eg 192.168.10.10) has no restrictions to outgoing internet access
- I have no ports forwarded
- If I try and add my VTO to DMSS via my external IP address, it fails, because my UDM blocks Dahua from accessing the internal address of my VTO (because external_IP:37777 is not forwarded to 192.168.10.10:37777)
From what you've described above
If you stop there, I don't know how you can add your VTO to DMSS via IP address.
- Your VTO has outgoing access to only 60 IP addresses (so actually more restrictive than my firewall rules)
- You say you have no ports forwarded
It would work if you used P2P (via some of those 60 allowed IP addresses)
Do you have any WAN IN rules ?
Do you have uPnP enabled ?
I am keeping this info in this posting of the review of the VTO2202 and VTH's in the hopes this may aid those down the road that encounter such problems.While manufacturers do sometimes use differing terminology, I use a UDM as well, and also have a selection of custom firewall rules, so we should be speaking the same language !
I'd be keen to work out what you're doing to make this work, as it would be good to avoid using the Dahua cloud if possible
- My VTO (eg 192.168.10.10) has no restrictions to outgoing internet access
- I have no ports forwarded
- If I try and add my VTO to DMSS via my external IP address, it fails, because my UDM blocks Dahua from accessing the internal address of my VTO (because external_IP:37777 is not forwarded to 192.168.10.10:37777)
From what you've described above
If you stop there, I don't know how you can add your VTO to DMSS via IP address.
- Your VTO has outgoing access to only 60 IP addresses (so actually more restrictive than my firewall rules)
- You say you have no ports forwarded
It would work if you used P2P (via some of those 60 allowed IP addresses)
Do you have any WAN IN rules ?
Do you have uPnP enabled ?
I am keeping this info in this posting of the review of the VTO2202 and VTH's in the hopes this may aid those down the road that encounter such problems.
As to your quetions...
WAN IN rules? None. UDM router uses IMPLICIT rules. None come in, AOK to go out.
I'd like to hear how other folks use their VTO notification config. I bet, my way seems...amateur because I am a amateur
I was going along the lines from the suggestion of a YouTuber who "says" IT guys for 10 years and knows Ubiquiti and UDM really well. He could be wrong! But I did a general search on how to block cameras from the internet... all said to use WAN OUT, so I ran with that. I do have a rule not allowing CAMERA subnet to talk to any other subnet already.I only asked about WAN IN because you said you had isolated your cameras by using WAN OUT.
As a general rule, you should never need to use WAN OUT rules.
It's best to place rules on incoming (from the perspective of the port), so LAN IN. See here for a good explanation.
Looking forward to hearing more precise details of your setup
I was going along the lines from the suggestion of a YouTuber who "says" IT guys for 10 years and knows Ubiquiti and UDM really well. He could be wrong! But I did a general search on how to block cameras from the internet... all said to use WAN OUT, so I ran with that. I do have a rule not allowing CAMERA subnet to talk to any other subnet already.
To use LAN IN to block camera internet? I think I can. Maybe it's better? I am no firewall specialist. Kinda rushed into the matter.
I just remembered...I did use the LAN IN to block camera network from going out. Then my UDM somehow broke and I had to do factory reset. I think I'll go back to LAN IN 'reject' for the cameras. On my todo list #12.Yes. You are hitting up the router to do unnecessary routing, when the traffic could be stopped before hitting that interface
have you figured this out yet? I had some personal drama appear and forgot about helping you with this.Yes. You are hitting up the router to do unnecessary routing, when the traffic could be stopped before hitting that interface
Nope. Reading your pages again, I think what you have done is allow your VTO outgoing access to call push notification services only, but then placed your phone on a VPN, and allow VTO->VPN routing, so the SIP call itself goes locally.have you figured this out yet? I had some personal drama appear and forgot about helping you with this.
Correct. VTO has outgoing internet access to Google Push notification ports ONLY. That is it for VTO internet access. Never want this thing phoning home or not blindly on the internet itself. But to utilize the push notification to my smartphone, it does HAVE to have access to the google (or for those with iOS) push service. Unfortunately, there are 61 IP's related to Google Push Notification Service (this is not the case with iOS) that I had to input into a single firewall group:Nope. Reading your pages again, I think what you have done is allow your VTO outgoing access to call push notification services only, but then placed your phone on a VPN, and allow VTO->VPN routing, so the SIP call itself goes locally.
My setup is simply to have the VTO/VTH on their own VLAN.
It has unrestricted outgoing access, so it can use the DMSS relay servers to call my phone when the intercom is pressed.
The VTO VLAN has no access to anything else on my network. That's good enough security for me at this point
There would be a battery trade-off for an always-on VPN connection on my phone; with an on-demand VPN connection, there would likely be call connection delays with initiating an on-demand VPN service over cellular, which may make the whole thing less usable (particularly for the wife !)
If the DMSS cloud becomes less reliable (it had a rough patch a few months ago), I'll reconsider all of this
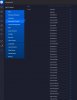
Unfortunately, there are 61 IP's related to Google Push Notification Service (this is not the case with iOS) that I had to input into a single firewall group
these are the IP addresses (with the /24's and such) given by Google. All those 6000+ IP's belong to Google.You do realise you have something like over 6000 IP addresses allowed in that screenshot ?
or should I say... this is the official Google listing response in what is required to hit their push services. I am just a slave so do not know any betterYou do realise you have something like over 6000 IP addresses allowed in that screenshot ?
