Okay, I am new at VPN stuff and have been doing a LOT of studying on all this, but some things are just not clear yet. On my new router, an ASUS RT-ACRH13 I want to set up the VPN with L2TP/IPsec because my smartphone already has a built-in option for L2TP/IPsec. Can anyone knowledgeable about this look at the spec sheet for my router at https://www.asus.com/us/Networking/RT-ACRH13/specifications/ and tell me if I can set up the VPN on my router for L2TP/IPsec so I'll be able to view the live camera feed from my security camera on my smartphone. If it is possible, is the VPN L2TP/IPsec stuff already in the router or do I have to download and install it ?
VPN Primer for Noobs
- Thread starter nayr
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Okay, did more research, let me know if this is not right, it seems the ASUS RT-ACRH13 does not have VPN itself, but allows VPN to work thru it and I still have to set up L2TP/IPsec VPN on my Windows 10 laptop ? I found this help page - How to set up L2TP/IPsec VPN on Windows 10 at https://www.bestvpnz.com/how-to-set-up-l2tpipsec-vpn-on-windows-10/ then after I set up that VPN on my laptop I would then do this from
page 70 of the router manual at http://m.setuprouter.com/router/asus/rt-acrh13/manual-2290.pdf which says:
4.3.6 NAT Passthrough
NAT Passthrough allows a Virtual Private Network (VPN) connection to pass through the router to the network clients. PPTP Passthrough, L2TP Passthrough, IPsec Passthrough and RTSP Passthrough are enabled by default. To enable / disable the NAT Passthrough settings, go to the Advanced Settings > WAN > NAT Passthrough tab. When done, click Apply.
page 70 of the router manual at http://m.setuprouter.com/router/asus/rt-acrh13/manual-2290.pdf which says:
4.3.6 NAT Passthrough
NAT Passthrough allows a Virtual Private Network (VPN) connection to pass through the router to the network clients. PPTP Passthrough, L2TP Passthrough, IPsec Passthrough and RTSP Passthrough are enabled by default. To enable / disable the NAT Passthrough settings, go to the Advanced Settings > WAN > NAT Passthrough tab. When done, click Apply.
looney2ns
IPCT Contributor
From the specs. VPN server : L2TP Pass-Through, PPTP Server, OpenVPN Server.
You want to use the OpenVPN built into your router. Then use the app, OpenVPN connect on your phone.
Post a screen shot of your routers VPN setup page for your router.
I don't see OpenVPN on our Windows phones, the window phone VPN setup page only lists 2 options, IKEv2 -or- "L2TP with IPsec" and we want to be able to view the live camera feed when away from our home WIFI, so does the phone HAVE to use the same program as the router VPN ? From what I just searched I don't think they made OpenVPN for windows phones yet. Is there an OpenVPN for windows phones and if not will either VPN option work with my windows phone ? PLEASE NOTE:....... I just remembered that Hikvision has a windows phone app that says it can connect remotely, so how would I set up my router VPN to work with this app - iVMS-4500 at Get iVMS-4500 - Microsoft Store where the app description says: iVMS-4500 mobile client software, which is designed for the mobile phone on the basis of Windows Phone 8.0, can be used to remotely monitor the live video from embedded DVR, NVR, network camera, network speed dome and encoder via wireless network, play back record files and realize PTZ control as well.
No...you are confused..the router has open vpn built in..you will not need to setup anything on your laptop unless you plan on using it remotely..
Okay, just trying to figure out if I need to set up the built in VPN on my router in a certain way to work with the remote viewing windows mobile app iVMS-4500, don't mean to be a pest with all my questions, I keep researching on my own but still am not yet totally sure how to proceed yet, I'll keep researching, but any ideas are appreciated too

Okay, found these links for help with remote view setup for iVMS-4500 hopefully what they suggest is correct - http://www.hikvision.com/ueditor/net/upload/2016-05-24/729538a0-6d88-43d5-8ce5-211dcea316da.pdf AND Hangzhou Hikvision Digital Technology Co. Ltd.
fenderman
Staff member
- Mar 9, 2014
- 36,891
- 21,415
you are confused about the basics of vpn...when you are connected via vpn your phone thinks its on the local network...nothing special to do. use local ip.Okay, just trying to figure out if I need to set up the built in VPN on my router in a certain way to work with the remote viewing windows mobile app iVMS-4500, don't mean to be a pest with all my questions, I keep researching on my own but still am not yet totally sure how to proceed yet, I'll keep researching, but any ideas are appreciated too
you are confused about the basics of vpn...when you are connected via vpn your phone thinks its on the local network...nothing special to do. use local ip.
Sorry, I'm trying to understand this stuff, so all I have to do is to set things up according to the ivms-4500 viewer app instructions at http://www.hikvision.com/ueditor/net/upload/2016-05-24/729538a0-6d88-43d5-8ce5-211dcea316da.pdf ? In addition do I still need to go into the VPN settings on my phone and select "L2TP with IPsec" or is that not necessary with the ivms-4500 app being on my phone ?
Mike A.
Known around here
- May 6, 2017
- 4,201
- 7,069
Separate things. The VPN provides a secured connection into your network. You set up the server side on your router and set up the client side on your phone or other device. When connected, that effectively puts your phone as a device on your local network. From there, software, app, etc., need to be set up in a way to do whatever it is that they do. Your IP for those apps will be a local IP and destinations on your network will be local IPs. So instead of pointing them to whateverhost@somedomain.com, you'd point them to 192.168.x.x or whatever you use as a local IP addressing scheme.
In order to connect remotely, you'll also want to set up a dynamic DNS service so that you can connect by name to your IP vs number as the latter may change. The VPN (not apps) then will be pointed to that host.
In order to connect remotely, you'll also want to set up a dynamic DNS service so that you can connect by name to your IP vs number as the latter may change. The VPN (not apps) then will be pointed to that host.
Last edited:
Separate things. The VPN provides a secured connection into your network. You set up the server side on your router and set up the client side on your phone or other device. When connected, that effectively puts your phone as a device on your local network. From there, software, app, etc., need to be set up in a way to do whatever it is that they do. Your IP for those apps will be a local IP and destinations on your network will be local IPs. So instead of pointing them to whateverhost@somedomain.com, you'd point them to 192.168.x.x or whatever you use as a local IP addressing scheme.
In order to connect remotely, you'll also want to set up a dynamic DNS service so that you can connect by name to your IP vs number as the latter may change. The VPN (not apps) then will be pointed to that host.
Okay, thanks, I think it's getting a little clearer in my mind now, so before I set up the stuff as you explained, I first should get a dynamic DNS like from
noip at Free Dynamic DNS - Managed DNS - Managed Email - Domain Registration - No-IP or should I set the other stuff up first or does it matter which order I do stuff in ?
Mike A.
Known around here
- May 6, 2017
- 4,201
- 7,069
Doesn't make much difference. The DDNS just needs to be in place to resolve your outside IP when you go looking for it. You can set up the rest and use your known outside IP without having DDNS set up if you want. It's basically just a lookup that saves you from having to track what that address is.
Doesn't make much difference. The DDNS just needs to be in place to resolve your outside IP when you go looking for it. You can set up the rest and use your known outside IP without having DDNS set up if you want. It's basically just a lookup that saves you from having to track what that address is.
Okay, thanks !
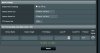
Okay, been searching the forum for anything I didn't yet know to do, one thread said to not have ANY Upnp enabled, I changed it to no on my router, I guess I'll need to do the same on the ivms-4200 interface for my camera too. Here's some screen shots showing how things are set up right now, not sure if I still need to make any further changes before connecting my camera into the network.

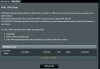
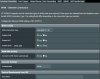
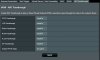
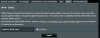




Last edited:
Wanted to add to my post below, from what I read in the forum that "port forwarding" is not recommended so I have that off (see screen shots below and let me know if anything might need adjusted, remember, I am new at IP cameras and vpn stuff)
Okay, been searching the forum for anything I didn't yet know to do, one thread said to not have ANY Upnp enabled, I changed it to no on my router, I guess I'll need to do the same on the ivms-4200 interface for my camera too. Here's some screen shots showing how things are set up right now, not sure if I still need to make any further changes before connecting my camera into the network.
View attachment 22980
View attachment 22981
View attachment 22982
View attachment 22983
View attachment 22985
View attachment 22986
Mike A.
Known around here
- May 6, 2017
- 4,201
- 7,069
Wanted to add to my post below, from what I read in the forum that "port forwarding" is not recommended so I have that off (see screen shots below and let me know if anything might need adjusted, remember, I am new at IP cameras and vpn stuff)
Most of that looks as it should but you'll need to turn OpenVPN on. That's your VPN server. Can't see how that's set from your pic.
UPnP should be turned off at the router. That will prevent anything like your cams from forcing things open on their own. You should turn it off on the devices as well but some don't necessarily follow what you set so killing it at the router makes sure. Also turn off any P2P-type functions in the cams (unless you're using it) to keep things from 'phoning home.' Again, some try to even when you've turned such things off on the cam.
Port Forwarding should be off as you have it unless you have some specific need. Coming in via VPN typically not. Also check that Port Trigger and DMZ are turned off.
You can use the Asus DDNS instead of No-IP. Either works. No-IP will work in some cases where the Asus DDNS doesn't (double NAT behind another router) but otherwise basically the same.
Under Administration > System, make sure that "Enable Web access from WAN" is turned off (permits remote access to the same pages that you're looking at). Also check that telnet is turned off. You can flip it on/off as you need it.
Under IPv6 set that to disabled unless you have some reason to enable it.
Under Firewall, it should be set on. DDOS doesn't matter much but generally I'll leave that turned on. Respond to ICMP doesn't matter much but generally I turn it off just so that there' s not an immediate ping picked up by port scanners. Harder scans still will pick up that there's something there.
Separate consideration but under Wireless make sure that WPS is set to off.
Depending on how you're set up, some other things that you can do to harden it a little more and you also can block Internet access for specific devices, either erase or plug with nonsense values the gateway and DNS server settings on the devices, set up VLANs, etc., to keep things segregated and from getting in/out but that's kind of a next step. Get the basics working first.
Most of that looks as it should but you'll need to turn OpenVPN on. That's your VPN server. Can't see how that's set from your pic.
UPnP should be turned off at the router. That will prevent anything like your cams from forcing things open on their own. You should turn it off on the devices as well but some don't necessarily follow what you set so killing it at the router makes sure. Also turn off any P2P-type functions in the cams (unless you're using it) to keep things from 'phoning home.' Again, some try to even when you've turned such things off on the cam.
Port Forwarding should be off as you have it unless you have some specific need. Coming in via VPN typically not. Also check that Port Trigger and DMZ are turned off.
You can use the Asus DDNS instead of No-IP. Either works. No-IP will work in some cases where the Asus DDNS doesn't (double NAT behind another router) but otherwise basically the same.
Under Administration > System, make sure that "Enable Web access from WAN" is turned off (permits remote access to the same pages that you're looking at). Also check that telnet is turned off. You can flip it on/off as you need it.
Under IPv6 set that to disabled unless you have some reason to enable it.
Under Firewall, it should be set on. DDOS doesn't matter much but generally I'll leave that turned on. Respond to ICMP doesn't matter much but generally I turn it off just so that there' s not an immediate ping picked up by port scanners. Harder scans still will pick up that there's something there.
Separate consideration but under Wireless make sure that WPS is set to off.
Depending on how you're set up, some other things that you can do to harden it a little more and you also can block Internet access for specific devices, either erase or plug with nonsense values the gateway and DNS server settings on the devices, set up VLANs, etc., to keep things segregated and from getting in/out but that's kind of a next step. Get the basics working first.
Thanks, your help is really appreciated, I'll check those settings you mentioned, but one concern - you said to turn OpenVPN on, we use windows phones, and unless I was misunderstanding what I read elsewhere, you must also have OpenVPN on your phone for it to connect with OpenVPN on your router, but OpenVPN does not yet have an app for Windows phones.
My windows phone VPN setup page only lists 2 options, IKEv2 -or- "L2TP with IPsec" and we just want to be able to view the live camera feed when away from our home WIFI.
We have a Hikvision ip camera and Hikvision has a windows phone app that says it can connect remotely, so how would I set up my router VPN to work with this app - iVMS-4500 at Get iVMS-4500 - Microsoft Store
The app description says: iVMS-4500 mobile client software, which is designed for the mobile phone on the basis of Windows Phone 8.0, can be used to remotely monitor the live video from embedded DVR, NVR, network camera, network speed dome and encoder via wireless network, play back record files and realize PTZ control as well.
Mike A.
Known around here
- May 6, 2017
- 4,201
- 7,069
Thanks, your help is really appreciated, I'll check those settings you mentioned, but one concern - you said to turn OpenVPN on, we use windows phones, and unless I was misunderstanding what I read elsewhere, you must also have OpenVPN on your phone for it to connect with OpenVPN on your router, but OpenVPN does not yet have an app for Windows phones.
My windows phone VPN setup page only lists 2 options, IKEv2 -or- "L2TP with IPsec" and we just want to be able to view the live camera feed when away from our home WIFI.
That's fine. Most have moved to OpenVPN but if that's what you have, that's what you have. Better than openly forwarding ports to cams.
We have a Hikvision ip camera and Hikvision has a windows phone app that says it can connect remotely, so how would I set up my router VPN to work with this app - iVMS-4500 at Get iVMS-4500 - Microsoft Store
The app description says: iVMS-4500 mobile client software, which is designed for the mobile phone on the basis of Windows Phone 8.0, can be used to remotely monitor the live video from embedded DVR, NVR, network camera, network speed dome and encoder via wireless network, play back record files and realize PTZ control as well.
Don't know that app but it should work in the same way that I described above. You'll make the secured connection to your network via the VPN addressed either specifically by IP or by host name using a DDNS service. The app then will run using that for its connectivity to your network. It will have what is effectively a local IP address so devices on your network will be accessed by local IP address (vs outside public IP : port or hostname.com : port). i.e., You'd set the software to look for 192.168.x.x with port settings however they need to be set. That's assuming that the app is not using a P2P-type approach, which from one of the comments it doesn't appear to. Again, don't know it though. Someone else may have better info re that.
That's fine. Most have moved to OpenVPN but if that's what you have, that's what you have. Better than openly forwarding ports to cams.
Don't know that app but it should work in the same way that I described above. You'll make the secured connection to your network via the VPN addressed either specifically by IP or by host name using a DDNS service. The app then will run using that for its connectivity to your network. It will have what is effectively a local IP address so devices on your network will be accessed by local IP address (vs outside public IP : port or hostname.com : port). i.e., You'd set the software to look for 192.168.x.x with port settings however they need to be set. That's assuming that the app is not using a P2P-type approach, which from one of the comments it doesn't appear to. Again, don't know it though. Someone else may have better info re that.
Okay, thanks, I was trying to figure this out as much as possible on my own, but there are so many options/variables it's difficult to be sure what is right for my equipment. (being on a budget on social security I needed to avoid the added expense of hiring a professional installer
That's fine. Most have moved to OpenVPN but if that's what you have, that's what you have. Better than openly forwarding ports to cams.
Don't know that app but it should work in the same way that I described above. You'll make the secured connection to your network via the VPN addressed either specifically by IP or by host name using a DDNS service. The app then will run using that for its connectivity to your network. It will have what is effectively a local IP address so devices on your network will be accessed by local IP address (vs outside public IP : port or hostname.com : port). i.e., You'd set the software to look for 192.168.x.x with port settings however they need to be set. That's assuming that the app is not using a P2P-type approach, which from one of the comments it doesn't appear to. Again, don't know it though. Someone else may have better info re that.
Okay, just want to be sure I am understanding correctly, so on my windows phone VPN setup page I can choose "L2TP with IPsec" and on the router I don't have to turn on the OpenVPN ? .....and that the "L2TP with IPsec" setting I choose on my windows phone VPN setup page will allow my phone to connect to my LAN (and camera on the LAN) since on the router page below "L2TP Passthrough" and "IPsec Passthrough" were already enabled ?
View attachment 22983
