Are these intrusions or uninvited guests?
- Thread starter petere10
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
sebastiantombs
Known around here
If you're port forwarding shut it off and use a VPN for accessing your system from the outside world. If UPnP is enabled, anywhere, shut it off. I wouldn't be happy, at all, seeing that.
uPNP is OFF on the router. The only access set up is the web server through BI. Is that a problem? The only DIRECT access to the internet is on a different sub-net range through WiFi, and the cameras don't even go through the router. I'm a bit mystified.
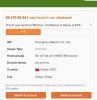
Using reverse IP lookup at reverseip.domaintools.com shows BOTH IP addresses as hosting no domains (ie, no results found). Is the BI web server safe??
The first IP is out of Taiwan and the 2nd is out of Italy. I would say you probably came up in a portscan because you have exposed your setup on the Internet. You must have ports opened up that are facilitating this. You should look into VPN access and closing up those ports.
I get the first IP address out of the Netherlands...
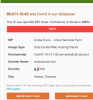
BI exposes port 81.....
I just disabled external IP access for BI. See if that makes a change
BI exposes port 81.....
I just disabled external IP access for BI. See if that makes a change
sebastiantombs
Known around here
sebastiantombs
Known around here
You're still leaving port 81 OPEN to the outside world to attach to you're PC. Port 81 is in the range and BI is listening on that port, it hears (gets) a request and they're in, nice and cozy like a bug in a rug.
I did mention that I just deleted my external IP address from BI web server. I would assume that BI will now only serve to my local IP addresses?? Please correct me if I'm wrong. I'm happy to PM my external IP to you if you can help me understand this.You're still leaving port 81 OPEN to the outside world to attach to you're PC. Port 81 is in the range and BI is listening on that port, it hears (gets) a request and they're in, nice and cozy like a bug in a rug.
Thanks
Pete
If BI web server is THAT VULNERABLE, why include it?
It's not the webserver that is vulnerable, it's the fact that you exposed it to the Internet which makes you vulnerable to scans/probes from others on the Internet. If you would like to view BI remotely, look at the wiki and read the VPN primer and look into setting up a VPN.
sebastiantombs
Known around here
Any web server has the same vulnerabilities. Normally a web server is behind some form of firewall and monitored, to some degree, to make sure that attacks are seen quickly and stopped.
Great siteGoogle grc shields up and run the common ports scan from their site and see what the report shows for open ports.
1. Target site (my router) actively rejected uPNP probes
2. 80 / 81 and 443 are open
3. Port 139 does not appear to exist and unable to connect to NetBios
Great site
1. Target site (my router) actively rejected uPNP probes
2. 80 / 81 and 443 are open
3. Port 139 does not appear to exist and unable to connect to NetBios
OK - there is your answer. Those ports are open somehow. You need to look into why that is on your router/firewall.
If I'm correct, if you close port 80, you won't get any internet....OK - there is your answer. Those ports are open somehow. You need to look into why that is on your router/firewall.
Ports are opened for the purposes of remote access, inbound not access outbound from your network. Closing that up will not affect your ability to surf the Internet.
d.lux
Getting the hang of it
There are consumer grade routers coming out with active firewalls/AV stuff now...
I want to say Netgears' interface looks clean, alas they want to charge for it...
I know the TPLink stuff is free, but if you want to get into the nitty gritty, pick up a pfSense box...
Pretty cool stuff....
I want to say Netgears' interface looks clean, alas they want to charge for it...
I know the TPLink stuff is free, but if you want to get into the nitty gritty, pick up a pfSense box...
Pretty cool stuff....