*edit* 01Dec17 Text attachments now in Windows form instead of Linux form so they format properly.
*edit* 21Dec17 To make the process of unbricking and upgrading much easier to use, this has been superseded by the brickfixV2 method here : R0 / DS-2CD2x32 BrickfixV2 brick recovery and full upgrade tool - enhanced.
I was not going to post these details in public, to reduce the chance of Hikvision blocking them in future firmware - though no such inhibitions in private, quite busy on the topic!
But then this happened : Hikvision no longer selling to the end user
See also this link and the attached PDF in this post.
HikVision End of Supply 4-8-17
It's just another example of how Hikvision continues to treat their customers with contempt in their misguided and ultimately doomed 'Prop up the Authorised Resellers inflated margins' tactics.
Shame on you, Hikvision, what an awful way to do business!
Some other, for a $multi-billion business, rather un-business-like activities:
Putting Blogger Anti-Hikvision Rhetoric in Perspective
Blogger’s Cyberbullying Mission Tiresome, Destined to Fail
Hikvision Attacks IPVM
Hikvision Blogs About IPVM: "Putting Blogger Anti-Hikvision Rhetoric In Perspective"
I'm sure their main rival Dahua will be quite pleased to fill the gap that Hikvision seem to be vacating.
If the way that the postings volume in ipcamtalk.com has shifted to the now dominant Dahua away from Hikvision over the past year is an indication, maybe the customer sentiment is already moving against Hikvision.
So it's time to provide a roundup of a little help to Hikvision's stranded and unsupported R0 camera customers.
You bought your DS-2CD2x32-I camera at low cost off eBay or Aliexpress and upgraded the firmware to the published 5.3.0 version.
The web GUI menus changed to Chinese. Your Hikvision NVR now rejects the camera with a 'Language mismatch' error. Your camera no longer responds - it's bricked.
You've fallen into a deliberate Hikvision trap aimed at on-line purchasers of Chinese market cameras running seller-installed 'Hacked to English' firmware.
Go to the @whoslooking Custom Firmware Downgrader 5.3.0 Chinese to 5.2.5 English and get back to English menus.
To fix Chinese day-of-the-week or 'Language mismatch' errors connecting your 5.2.5 firmware camera to your NVR, go to the classic mtd hack from @whoslooking
Hikvision 5.2.5 & 5.2.8 Full English (INC DAYS OF WEEK) mtd Hack
If you saw the Hikvision security advice to update your camera firmware following the high-severity security vulnerability / backdoor found and reported by forum member @montecrypto and it bricked - you have fallen into the Hikvision deliberate Catch-22 trap.
Backdoor found in Hikvision cameras
Hangzhou Hikvision Digital Technology Co. Ltd.
(I wonder if the ISC-CERT referenced here is deliberately mistyped?)
Hangzhou Hikvision Digital Technology Co. Ltd.
A perfect 10 out of 10! And 8.8 for putting passwords in plain text in the configuration file. Dohh..
Hikvision Cameras | ICS-CERT
NVD - CVE-2017-7923
DS-2CD2432F-IW 3MP firmware issue after trying to upgrade to 5.4
These are very good reasons to update the camera firmware. And shame on you Hikvision for putting in measures that block this.
Now your camera won't run the updated/fixed firmware / won't downgrade as a downgrade block has been implemented. It's bricked!
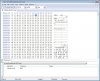
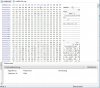
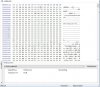
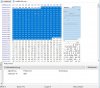
Fortunately - as there is a lot of this around - there is a fix for the problem, the 'Brickfix tool'.
Tool and instructions in the attached file Brick_fix_tool.txt
Have you found that following email provider security improvements, your camera with older firmware will no longer send gmail or GMX notifications?
You know there is a fix for this, and bug-fixes and various serious security fixes in updated firmware, but you can't apply it as the Hikvision firmware has code that will stop it running on cameras bought at low cost on-line or from other than authorised resellers.
You could try the attached 'enhanced_mtd_hack.txt' guide which has been pretty successful in allowing the 'non-upgradable' cameras to be fully upgraded and making them safer and better to use. Which is something Hikvision should be encouraging, not blocking. In my view.
*edit* 21Dec17 To make the process of unbricking and upgrading much easier to use, this has been superseded by the brickfixV2 method here : R0 / DS-2CD2x32 BrickfixV2 brick recovery and full upgrade tool - enhanced.
I was not going to post these details in public, to reduce the chance of Hikvision blocking them in future firmware - though no such inhibitions in private, quite busy on the topic!
But then this happened : Hikvision no longer selling to the end user
See also this link and the attached PDF in this post.
HikVision End of Supply 4-8-17
It's just another example of how Hikvision continues to treat their customers with contempt in their misguided and ultimately doomed 'Prop up the Authorised Resellers inflated margins' tactics.
Shame on you, Hikvision, what an awful way to do business!
Some other, for a $multi-billion business, rather un-business-like activities:
Putting Blogger Anti-Hikvision Rhetoric in Perspective
Blogger’s Cyberbullying Mission Tiresome, Destined to Fail
Hikvision Attacks IPVM
Hikvision Blogs About IPVM: "Putting Blogger Anti-Hikvision Rhetoric In Perspective"
I'm sure their main rival Dahua will be quite pleased to fill the gap that Hikvision seem to be vacating.
If the way that the postings volume in ipcamtalk.com has shifted to the now dominant Dahua away from Hikvision over the past year is an indication, maybe the customer sentiment is already moving against Hikvision.
So it's time to provide a roundup of a little help to Hikvision's stranded and unsupported R0 camera customers.
You bought your DS-2CD2x32-I camera at low cost off eBay or Aliexpress and upgraded the firmware to the published 5.3.0 version.
The web GUI menus changed to Chinese. Your Hikvision NVR now rejects the camera with a 'Language mismatch' error. Your camera no longer responds - it's bricked.
You've fallen into a deliberate Hikvision trap aimed at on-line purchasers of Chinese market cameras running seller-installed 'Hacked to English' firmware.
Go to the @whoslooking Custom Firmware Downgrader 5.3.0 Chinese to 5.2.5 English and get back to English menus.
To fix Chinese day-of-the-week or 'Language mismatch' errors connecting your 5.2.5 firmware camera to your NVR, go to the classic mtd hack from @whoslooking
Hikvision 5.2.5 & 5.2.8 Full English (INC DAYS OF WEEK) mtd Hack
If you saw the Hikvision security advice to update your camera firmware following the high-severity security vulnerability / backdoor found and reported by forum member @montecrypto and it bricked - you have fallen into the Hikvision deliberate Catch-22 trap.
Backdoor found in Hikvision cameras
Hangzhou Hikvision Digital Technology Co. Ltd.
(I wonder if the ISC-CERT referenced here is deliberately mistyped?)
Hangzhou Hikvision Digital Technology Co. Ltd.
A perfect 10 out of 10! And 8.8 for putting passwords in plain text in the configuration file. Dohh..
Hikvision Cameras | ICS-CERT
NVD - CVE-2017-7923
DS-2CD2432F-IW 3MP firmware issue after trying to upgrade to 5.4
These are very good reasons to update the camera firmware. And shame on you Hikvision for putting in measures that block this.
Now your camera won't run the updated/fixed firmware / won't downgrade as a downgrade block has been implemented. It's bricked!
Fortunately - as there is a lot of this around - there is a fix for the problem, the 'Brickfix tool'.
Tool and instructions in the attached file Brick_fix_tool.txt
Have you found that following email provider security improvements, your camera with older firmware will no longer send gmail or GMX notifications?
You know there is a fix for this, and bug-fixes and various serious security fixes in updated firmware, but you can't apply it as the Hikvision firmware has code that will stop it running on cameras bought at low cost on-line or from other than authorised resellers.
You could try the attached 'enhanced_mtd_hack.txt' guide which has been pretty successful in allowing the 'non-upgradable' cameras to be fully upgraded and making them safer and better to use. Which is something Hikvision should be encouraging, not blocking. In my view.
Attachments
Last edited: