alastairstevenson
Staff member
There are quite a few steps. maybe a bit optimistic if you've not done this before.
I had a look out of curiosity, and found this slightly newer 3.1.6 firmware version here, 3 from the bottom: http://overseas.hikvision.com/en/download_89_p1.html
The digicap.dav is unusually large at 28MB, and using Hiktools to 'split' it yields a cramfs.img of 15MB. Strange. A closer look shows there are 2 cramfs.img images held in the digicap.dav, one 15MB and one 12MB
So I mounted these in Linux and sure enough there is a 100KB logo.tar.lzma file which might be a candidate to customise for the bootup image.
However - this 3.1.6 firmware is one of the series where the component files have been encoded or encrypted, which unfortunately inhibits the ability to change the contents.
The same is also true of the second cramfs.img that is held in the digicap.dav, also encrypted.
Your firmware at 3.1.1 is a little older. Maybe it pre-dates when encryption was introduced.
To examine you'd use the following steps:
In Windows, create a new folder under the one where the digicap.dav (and hiktools05r1.exe) is stored, lets call it 'contents'.
At a command prompt 'hiktools05r1 split digicap.dav contents'
This will extract cramfs.img (just the first one) into contents.
If you copy that into a Linux environment you should be able to mount it as a CRAMFS and examine the contents.
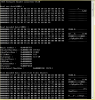
A simple way to check if the files are encoded is to use 'file *' and see which are listed as 'data'.
I had a look out of curiosity, and found this slightly newer 3.1.6 firmware version here, 3 from the bottom: http://overseas.hikvision.com/en/download_89_p1.html
The digicap.dav is unusually large at 28MB, and using Hiktools to 'split' it yields a cramfs.img of 15MB. Strange. A closer look shows there are 2 cramfs.img images held in the digicap.dav, one 15MB and one 12MB
So I mounted these in Linux and sure enough there is a 100KB logo.tar.lzma file which might be a candidate to customise for the bootup image.
However - this 3.1.6 firmware is one of the series where the component files have been encoded or encrypted, which unfortunately inhibits the ability to change the contents.
The same is also true of the second cramfs.img that is held in the digicap.dav, also encrypted.
Your firmware at 3.1.1 is a little older. Maybe it pre-dates when encryption was introduced.
To examine you'd use the following steps:
In Windows, create a new folder under the one where the digicap.dav (and hiktools05r1.exe) is stored, lets call it 'contents'.
At a command prompt 'hiktools05r1 split digicap.dav contents'
This will extract cramfs.img (just the first one) into contents.
If you copy that into a Linux environment you should be able to mount it as a CRAMFS and examine the contents.
A simple way to check if the files are encoded is to use 'file *' and see which are listed as 'data'.