How to setup Dahua IVS with BlueIris?
- Thread starter Geomancer
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
astroshare
Getting the hang of it
Is this still broken? I have followed the instructions here and just keep getting "Events: Subscription 00000190" messages.
astroshare
Getting the hang of it
sebastiantombs
Known around here
astroshare
Getting the hang of it
Yes, but still the IVS won't trigger the camera. It's ok though. I think for now BI motion detection + AI TOOL are working fine for me. Thanks for your help.Sorry you're not having any luck. You did enable ONVIF events in the trigger profile, right?
Yes, but still the IVS won't trigger the camera. It's ok though. I think for now BI motion detection + AI TOOL are working fine for me. Thanks for your help.
So I just purchased two more cameras from Andy:
- IPC-T5442TM-AS
- System Version: V2.800.15OG004.0.R, Build Date: 2020-10-19
- IPC-T5442T-ZE
- System Version: V2.800.0000000.16.R, Build Date: 2020-05-29
Neither of these work with IVS. They do work with just motion detection from the camera settings.
My older IPC-T5442TM-AS with System Version V2.800.0000000.20.R, Build Date: 2020-09-03 DOES still work.
@EMPIRETECANDY did IVS break with newer System Versions and BI? I am on BI 5.3.7.13 and the 2020-09-03 build works but not the 2020-10-19 build.
astroshare
Getting the hang of it
Mine is System Version V2.800.0000000.22.R, Build Date: 2020-11-19. It's the latest FW that was posted here.
Cavalier240
n3wb
- Dec 6, 2016
- 8
- 2
I know this post is several months old, but it made me raise an eyebrow while reading back through this thread... I'd like to hear your rationale behind saying there is no benefit to HTTPS. Defense in depth. including encrypting traffic, is always preferable on any network. I'm guessing you are assuming that cameras will be isolated (either physically or logically), but anything can be compromised, including a router/switch managing VLANS, a double-NIC NVR, etc. So why not be as secure as possible?There is absolutely no reason at all that you need an https connection to your camera. None. It provides zero benefit.
fenderman
Staff member
- Mar 9, 2014
- 36,891
- 21,415
If someone has direct access to your network who gives a crap how you connect to the camera - which likely is full of exploits anyway. The entire point of securing your network is to prevent a hacker from using your camera as an access point INTO your network not that the hacker wants to view your camera footage. If they are already there they dont need your cam. I have many setups where the cameras are left at default (back when hik/dahua allowed it in the firmware). If they were successful in hacking your vpn, passing through your vlans, hacking the dahua camera will be a joke. Https doesnt make the camera itself any more secure. Give me a single scenario where it would be beneficial.I know this post is several months old, but it made me raise an eyebrow while reading back through this thread... I'd like to hear your rationale behind saying there is no benefit to HTTPS. Defense in depth. including encrypting traffic, is always preferable on any network. I'm guessing you are assuming that cameras will be isolated (either physically or logically), but anything can be compromised, including a router/switch managing VLANS, a double-NIC NVR, etc. So why not be as secure as possible?
Cavalier240
n3wb
- Dec 6, 2016
- 8
- 2
Point taken. But I'd say that the point of securing your home network is not only to "prevent a hacker from using your camera as an access point INTO your network," as you said. Instead, for me the main point of securing my network is to protect my data. And that means all of my data, including my camera streams since I have internal cameras. So for me, using HTTPS has more value than not using it, because more layers of defense doesn't hurt. I'm sure you have a reason for not using HTTPS, so where does it hurt? Is it a limitation of BI or some cameras?If someone has direct access to your network who gives a crap how you connect to the camera - which likely is full of exploits anyway. The entire point of securing your network is to prevent a hacker from using your camera as an access point INTO your network not that the hacker wants to view your camera footage. If they are already there they dont need your cam. I have many setups where the cameras are left at default (back when hik/dahua allowed it in the firmware). If they were successful in hacking your vpn, passing through your vlans, hacking the dahua camera will be a joke. Https doesnt make the camera itself any more secure. Give me a single scenario where it would be beneficial.
fenderman
Staff member
- Mar 9, 2014
- 36,891
- 21,415
its not a limitation of anything both BI and the cams support them. Its a complete waste of time because as I already explained. IPoint taken. But I'd say that the point of securing your home network is not only to "prevent a hacker from using your camera as an access point INTO your network," as you said. Instead, for me the main point of securing my network is to protect my data. And that means all of my data, including my camera streams since I have internal cameras. So for me, using HTTPS has more value than not using it, because more layers of defense doesn't hurt. I'm sure you have a reason for not using HTTPS, so where does it hurt? Is it a limitation of BI or some cameras?
a) the cameras firmware is FULL of exploits and they are patched months after discovery if ever
b) if someone has direct access to your network, your data is not secured by using https. ]
sympathize with your ocd. It doesnt hurt to create a 15 character password for your cams either, but its a complete waste of time. Knock yourself out, but dont fool yourself into thinking you are any more secure.
astroshare
Getting the hang of it
Just allow your cameras to talk only to your BI box and block all other traffic. That's how I have my pfsense rules setup.
Point taken. But I'd say that the point of securing your home network is not only to "prevent a hacker from using your camera as an access point INTO your network," as you said. Instead, for me the main point of securing my network is to protect my data. And that means all of my data, including my camera streams since I have internal cameras. So for me, using HTTPS has more value than not using it, because more layers of defense doesn't hurt. I'm sure you have a reason for not using HTTPS, so where does it hurt? Is it a limitation of BI or some cameras?
So millions of people around the world want the simplicity of Internet of Things (IoTs) to be easy to connect to their system and work. They do not want to deal with security. They wrongfully assume that because they bought it and all they have to do is scan an QR code, that all is good. A manufacturer also doesn't want to deal with endless phone calls from consumers asking how to set something up.
So these companies create these QR codes and magically the new device can be seen on the consumers app. Consumer is happy. But, this device has opened up the system to gain easy access to your entire network, usually through a port forward, opening a port, or something else. But regardless of the method, it opens up the system.
I have a friend that falls under this "I just want to plug it in and scan a code and it works" mindset. Many years ago she bought a Foscam wifi camera to monitor her front door. She plugged it in and pointed it out a 2nd story window and downloaded the Foscam app and scanned the QR code and magically she could see her camera.
A few years later she bought a wifi printer and again, simply dowloaded the app from the manufacturer and scanned the QR code and she could start printing.
One time in the middle of the night, she hears her printer printing a page. She thinks maybe she is dreaming or hearing things, so she thinks nothing of it and goes back to sleep. Next morning she gets up and the printed page says I SEE YOU and a picture of her from her Foscam was below it.
She changes her wifi password in case it was the peeping perv next door that she has caught looking at her from through her window and he guessed her password, which was password because she liked thing simple.

Problem still persists. She goes into Foscam app and changes the password to the camera. Problem still persists. She gets a new router. Problem still persists. She gets rid of camera and printer.
At some point Foscam issues a security vulnerability and issued a firmware update. Based on chatter on forums, basically the vulnerability was something like when logging into the camera with a web browser over HTTPS, the initial login to the site is done using SSL. But then it establishes a connection to the HTTPS port again (for the media service) and sends all of its commands unencrypted. This means the username and passwords are being sent unencrypted. While this was a security vulnerability found in Foscam, I suspect it is in others as well. I suspect this is how my friend was hacked and someone was sending pictures of her taken from her Foscam camera to her wifi printer that she set up using the QR code.
Many articles on this site and out on the internet show how vulnerable these devices can be. I remember seeing an article of a webpage showing like 75,000 video streams around the world that were hacked into because of these vulnerabilities. I know there is an article someone on this forum where someone posted that many of these cameras do send passwords totally unencrypted and wide open easy to see for anyone knowing what they are doing.
Do not assume that because it is a name brand that they actually have good security on these cameras or any device for that matter. Think about the typical end-user that just wants simplicity to connect. And then think how a company would go about that to provide that simplicity. End result is to provide that simplicity, it comes at a cost and that cost is security vulnerabilities, which is ironic for security cameras. But if it can happen to Amazon/Ring (which is a fairly large company), it can happen to anyone, especially all the no-name brands being sold on Amazon.
For that reason, most of us here prevent the cams from having access to the internet.
Last edited:
For those that are interested and struggling with this, I just got this working with my Amcrest camera. This works with 24/7 recording and alerts, in my case MMS to our phones.
Camera: Amcrest IP5M-T1179EW-28MM
Dahua Firmware: DH_IPC-HX25(8)XX-Molec_MultiLang_NP_V2.800.0000000.15.R.200313
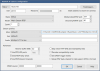
Settings under Camera Settings>Video>Configure are:
Make: Dahua
Model: *Main Stream RTSP
Discovery/ONVIF: port 80
Stream Profiles Main: /cam/realmonitor?channel={CAMNO}&subtype=0&authbasic={AUTH64}&proto=Onvif
Stream Profiles Sub: /cam/realmonitor?channel={CAMNO}&subtype=1&authbasic={AUTH64}&proto=Onvif
Check the box for: Get ONVIF trigger events
ONVIF source: 00000 (for both boxes)
Settings under Camera Settings>Trigger are:
Sources only check Camera's digital input or motion alarm and Trigger until reset
For MMS Messages
Settings under Camera Settings>Alerts
Fire when: This camera is triggered
Motion zones: Unchecked
Minimum time between alerts: I used 30 sec.
Then configure Actions On alert... (Configure as needed)
On the camera itself:
Event>Smart Plan: Enable IVS
Event>IVS
Create a new Intrustion rule and name it
Draw the area of intrest
Action chec Appears and Cross
Check Record
Check Snapshot
Event>Video Detection>Motion Detection Disable
Event>Video Detection>Motion Detection Disable
I think I hit the main sections for configuring IVS to work with Blue Iris. If I missed something or didnt explain something well enough, I apologize.
Camera: Amcrest IP5M-T1179EW-28MM
Dahua Firmware: DH_IPC-HX25(8)XX-Molec_MultiLang_NP_V2.800.0000000.15.R.200313
Settings under Camera Settings>Video>Configure are:
Make: Dahua
Model: *Main Stream RTSP
Discovery/ONVIF: port 80
Stream Profiles Main: /cam/realmonitor?channel={CAMNO}&subtype=0&authbasic={AUTH64}&proto=Onvif
Stream Profiles Sub: /cam/realmonitor?channel={CAMNO}&subtype=1&authbasic={AUTH64}&proto=Onvif
Check the box for: Get ONVIF trigger events
ONVIF source: 00000 (for both boxes)
Settings under Camera Settings>Trigger are:
Sources only check Camera's digital input or motion alarm and Trigger until reset
For MMS Messages
Settings under Camera Settings>Alerts
Fire when: This camera is triggered
Motion zones: Unchecked
Minimum time between alerts: I used 30 sec.
Then configure Actions On alert... (Configure as needed)
On the camera itself:
Event>Smart Plan: Enable IVS
Event>IVS
Create a new Intrustion rule and name it
Draw the area of intrest
Action chec Appears and Cross
Check Record
Check Snapshot
Event>Video Detection>Motion Detection Disable
Event>Video Detection>Motion Detection Disable
I think I hit the main sections for configuring IVS to work with Blue Iris. If I missed something or didnt explain something well enough, I apologize.
LOL.... thought I was going to lose my mind trying to figure out how to END a tripwire line!! RIGHT-CLICK--- Derrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrp
Ha - had the same problem! Took me hours to figure that out!
I'm lost on this part. I turn off Motion when I'm trying to use IVS. However, in a few hours I will see a lot of false alerts. So if I go back into the Dahua camera settings, I'll see that Motion is Enabled on its own once again! What?I'm not, no. Only IVS.
I would of been okay with the more overall "Smart Motion" option the newer firmware on my cameras has as it can filter for people and/or cars. However, if I turn that option on it also turns on the general motion detection and it's right back to false alerts. Not sure if that's a bug or not.
Dave Lonsdale
Pulling my weight
Yes, my older Dahuas do that. Turn the sensitivity to “0” and threshold to “100”. These settings are remembered.