Hey folks.
I have been reading a lot on this forum and i have some questions before making a move. I would like assistance from senior with experience in this domain it would be greatly appreciated.
As a quick and brief introduction, i got into this new home and i would like to setup a network that i will be able to properly add cameras to later on. The network must absolutely have a guest network (it's a feature i absolutely need here). From my understanding so far, the router should support both OpenVPN and IPCT DDNS. If possible i would like to know if routers can support Wireguard as a VPN solution because i am most familiar with it, but it's not really mentioned here in the forums from what i read.
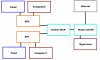
I currently have a TP-Link Archer2 AC750 which is not bad but i can't find any VPN support for it so i'm willing to change it. I also have a modem from the ISP which is connected to their router (a Zyxel router, i don't know the model). I also need to add a third router in another room for full coverage of the building. I also have a Cisco E4200v2 but considering it was a pain to make two routers from different companies use the same wifi networks (2.4 and 5ghz, the guest network with two different routers never worked), instead i think it would be best not to install it and properly plan and design what hardware to use.
So the plan here is to make a killer network with VPN support (openvpn or wireguard), IPCT DDNS support, high security, with three wifi networks with three of the same device. It also needs to be able to support cameras that will be added later.
My plan right now would be to have three times the same router. One will be connected to the modem as a gateway, the two other ones in two different rooms will be used both to replicated the same three wifi networks (guest, 2.4 and 5ghz) and used as switches for cabled computers (and cameras, eventually). I see a lot of people mention the Asus AC1900 RT-AC68U but it's 200$ + taxes in canada (230$ each, times three it's 700$!!!) so it's a little too expensive. The TP-Link Archer2 AC750 i have was 40 bucks (cheap lmao) but let's say i would be willing up to 120$ with taxes each routers.
Unfortunate it doesn't seem to support either VPN or DDNS.
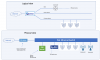
I think three routers will be sufficient as my terrain i need to cover with Wifi is 42 by 80 feets in a two stories building with basement. The main router (internet gateway) is in the basement, eastward, and the other two routers are located First floor west and first floor north.
Please let me know what you think!
Thanks!
I have been reading a lot on this forum and i have some questions before making a move. I would like assistance from senior with experience in this domain it would be greatly appreciated.
As a quick and brief introduction, i got into this new home and i would like to setup a network that i will be able to properly add cameras to later on. The network must absolutely have a guest network (it's a feature i absolutely need here). From my understanding so far, the router should support both OpenVPN and IPCT DDNS. If possible i would like to know if routers can support Wireguard as a VPN solution because i am most familiar with it, but it's not really mentioned here in the forums from what i read.
I currently have a TP-Link Archer2 AC750 which is not bad but i can't find any VPN support for it so i'm willing to change it. I also have a modem from the ISP which is connected to their router (a Zyxel router, i don't know the model). I also need to add a third router in another room for full coverage of the building. I also have a Cisco E4200v2 but considering it was a pain to make two routers from different companies use the same wifi networks (2.4 and 5ghz, the guest network with two different routers never worked), instead i think it would be best not to install it and properly plan and design what hardware to use.
So the plan here is to make a killer network with VPN support (openvpn or wireguard), IPCT DDNS support, high security, with three wifi networks with three of the same device. It also needs to be able to support cameras that will be added later.
My plan right now would be to have three times the same router. One will be connected to the modem as a gateway, the two other ones in two different rooms will be used both to replicated the same three wifi networks (guest, 2.4 and 5ghz) and used as switches for cabled computers (and cameras, eventually). I see a lot of people mention the Asus AC1900 RT-AC68U but it's 200$ + taxes in canada (230$ each, times three it's 700$!!!) so it's a little too expensive. The TP-Link Archer2 AC750 i have was 40 bucks (cheap lmao) but let's say i would be willing up to 120$ with taxes each routers.
Unfortunate it doesn't seem to support either VPN or DDNS.
I think three routers will be sufficient as my terrain i need to cover with Wifi is 42 by 80 feets in a two stories building with basement. The main router (internet gateway) is in the basement, eastward, and the other two routers are located First floor west and first floor north.
Please let me know what you think!
Thanks!