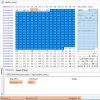
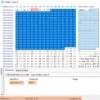
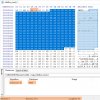
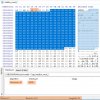
alastair@PC-I5 ~ $ ssh admin@192.168.1.105
admin@192.168.1.105's password:
repacked
BusyBox v1.19.3 (2017-01-13 20:51:32 CST) built-in shell (ash)
Enter 'help' for a list of built-in commands.
# prtHardInfo
Start at 2020-04-19 16:54:07
Serial NO :DS-2CD2432F-IW20141105CCCH487719881
V5.4.5 build 170123
NetProcess Version: 1.6.1 [17:24:18-Jan 13 2017]
Db Encrypt Version: 65537
hardwareVersion = 0x0
hardWareExtVersion = 0x0
encodeChans = 1
decodeChans = 1
alarmInNums = 1
alarmOutNums = 1
ataCtrlNums = 0
flashChipNums = 0
ramSize = 0x4000000
networksNums = 1
language = 1
devType = 0x9812
net reboot count = 0
Path: .
Working Copy Root Path: /usr/local/jenkins/workspace/Frontend_BaseLine_Publish_Build_InterfaceII/2539
URL: https://192.0.0.140/Camera/Platform/Branches/branches_frontend_software_platform/IPC_develop_branch/ipc_5.4.0_R0
Repository Root: https://192.0.0.140/Camera
Repository UUID: df2d70c3-7593-7941-af1e-571b313c0946
Revision: 253120
Node Kind: directory
Schedule: normal
Last Changed Author: liudan9
Last Changed Rev: 253065
Last Changed Date: 2017-01-23 17:45:28 +0800 (Mon, 23 Jan 2017)
#
#
#
# cd /home
# df -h
Filesystem Size Used Available Use% Mounted on
rootfs 7.9M 7.6M 342.0K 96% /
/dev/root 7.9M 7.6M 342.0K 96% /
udev 46.3M 76.0K 46.3M 0% /dev
/dev/ubi1_0 19.8M 13.2M 5.6M 70% /dav
/dev/ubi3_0 1.3M 160.0K 1.0M 13% /davinci
/dev/ubi4_0 1.3M 132.0K 1.0M 11% /config
#
# mount
rootfs on / type rootfs (rw)
/dev/root on / type ext2 (rw,relatime)
proc on /proc type proc (rw,relatime)
sysfs on /sys type sysfs (rw,relatime)
ramfs on /home type ramfs (rw,relatime)
udev on /dev type tmpfs (rw,relatime)
devpts on /dev/pts type devpts (rw,relatime,mode=600)
/dev/ubi1_0 on /dav type ubifs (rw,relatime)
/dev/ubi3_0 on /davinci type ubifs (rw,relatime)
/dev/ubi4_0 on /config type ubifs (rw,relatime)
#
# ls -al /mnt
drwxrwxrwx 13 root root 1024 Jan 13 2017 .
drwxr-xr-x 20 root root 1024 Apr 21 2020 ..
drwxrwxrwx 2 root root 1024 Jan 13 2017 mmc01
drwxrwxrwx 2 root root 1024 Jan 13 2017 mmc02
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs0
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs00
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs01
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs02
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs03
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs04
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs05
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs06
drwxrwxrwx 2 root root 1024 Jan 13 2017 nfs07
# mount -t nfs -o nolock 192.168.1.201:/cctv1 /mnt/nfs00
# ls -al /mnt/nfs00/c*.sh
-rwxrwxrwx 1 503 100 1579 Apr 21 15:41 /mnt/nfs00/checksum.sh
#
#
# cat /dev/mtd6ro > mtdfile
# ls -al
drwxr-xr-x 6 root root 0 Apr 21 16:56 .
drwxr-xr-x 20 root root 1024 Apr 21 16:38 ..
drwxr-xr-x 2 root root 0 Apr 19 16:53 applib
-rwxrwxrwx 1 root root 6674 Apr 19 16:53 initrun.sh
-rw-r--r-- 1 root root 524288 Apr 21 16:56 mtdfile
---------- 1 root root 0 Apr 19 16:53 pidfile
drwxr-xr-x 2 root root 0 Apr 19 16:53 process
drwxr-xr-x 2 3008 3008 0 Apr 19 16:53 sound
drwxr-xr-x 5 root root 0 Apr 19 16:53 webLib
#
# /mnt/nfs00/checksum.sh mtdfile
/mnt/nfs00/checksum.sh: line 43: syntax error: bad for loop variable
#
# rm mtdfile
# umount /mnt/nfs00
# Connection to 192.168.1.105 closed.
alastair@PC-I5 ~ $