TLDR; button press detection through software is possible! You will ned: a "fancy" firewall (I'm using a Mikrotik) + socat + bash script.
Initially when I wanted button press detection, I installed the current sensor Szc23-No-Al-Ch as described by
@tommyd75 and
@pete_c, and attached a zigbee button to it. It worked, but the major issue was that it didn't fit in my chime and I had nowhere to hide it, so it didn't pass the WAF test.
Of course the ideal solution would be to modify the firmware, but I am not versed in those skills.
@scruzloose33 wrote earlier in this thread that upon a button press, there was a DNS query to alarm.use.s3.amazonaws.com. I came to the same conclusion watching pihole logs, but on subsequent button presses there was no DNS query. Maybe the doorbell is caching the result.
I could've set up an A record in my lan DNS to point alarm.use.s3.amazonaws.com to the IP of a local machine listening on 443 for connections, but that would also have broken the normal "Answer Doorbell Call" function in the app, which I needed to keep working.
I quickly discovered that
dig alarm.use.s3.amazonaws.com yielded different addresses on pretty much every call, but they were always in the same two /16 subnets. I setup these subnets in an address list in my firewall. They are specific to my region, and if they were to change I would need to update my firewall rules.
Here is where the magic happens: the mikrotik firewall has an action=sniff-tzsp in the mangle chain. It's usually meant to send packets to a tzsp client such as Wireshark. But I chose to just use it as a sort of "knock". It sends one packet to a host where I have socat running. When socat detects the packet, it runs a script. And that's it!
Implementation
In your linux/macos terminal, run dig alarm.use.s3.amazonaws.com a few times.
Alternatively if you don't have dig, you can use your browser, go to
Dig (DNS lookup) and lookup alarm.use.s3.amazonaws.com a few times.
On the Mikoritk:
# add the list of addresses for alarm.use.s3.amazonaws.com (replace x.x with your results from above)
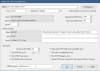
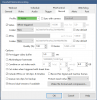
/ip firewall address-list
add address=x.x.0.0/16 list=alarms3
add address=x.x.0.0/16 list=alarms3
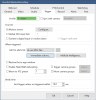
/ip firewall mangle
add action=sniff-tzsp chain=forward comment=doorbell connection-state=new dst-address-list=alarms3 sniff-target=IP-OF-SOCAT sniff-target-port=37008 src-address=IP-OF-DOORBELL
On a Pi or any other 24/7 server you have:
socat -u udp-l:37008,fork system:/home/youruser/dingdong-front.sh
Later you can install as a service. I used
GitHub - asaif/socat-init: Debain LSB init for socat.
/home/youruser/dingdong-front.sh contains whatever you want to happen when the doorbell is pressed. In my case, I wanted to trigger an entry point to a Nodered flow, so I have:
#!/bin/sh
curl -s https://IP-OF-NODERED:1880/dingdong-front > /dev/null
This triggers a flow httpin -> mqtt which publishes on a topic defined by the MQTT Link for a Virtual Switch in Hubitat. Hubitat picks it up and notifies the household.
I also have a second mangle going to port 37009, hitting another instance of socat listening on 37009 with a script hitting the dingdong-side httpin of the same Nodered flow.
Convoluted? Yes. Does it work and pass the WAF test? YASSS!!