Hi IP CAM crowd!
In the past weeks I have learned a lot by reading all the posts, linked pages and of course by playing a lot with the IP CAM and all the
tools, telnet, port scanners, routers, IP address management, port forwarding, etc., editors,,,,
My hardware: H264-HI3518E_50H10L_S39
Thanks a lot for all of your valuable contributions, efforts and posting of your wisdom! Solved the IP address issues, explored some depths of the TELNET and sofia, explored the config files, learned how to generate SSL certificates. Learned that I don’t need IE with active X. Really getting to like the Android app : tinyCam Pro.
As most of you concluded: the picture is great for the money spent. So what the issue?
My remaining open issues circle around safety and not the basic function:
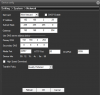
- Email setup: SMPT with SSL does not work
- Can’t enable HTTPS
- Unsure if the Chinese cloud services are active / listening / get reported to - even when not opted in? (Probably a good Idea to block the IPs of XMEYE
 ? )
? )
- Are all the CMS tools safe? Do they have backdoors?
- As I understand when using the media port rtsp streaming the user name and the password are transmitted in clear text over the network / internet. As a Post stated that on the ONVIF port nothing is or can be encrypted or even password protected. Even in your own private net it might be good idea to run the IP cam on a separate sub-net.
My workaround: for connecting the RTSP stream of an operator-with-password-protected-media-port forwarded from LAN to WAN I am using a VPN tunnel. However in case the VPN is not on and the Viewer software is trying to connect to the forwarded ports the log-in user name + PWD will be leaked into the infinite depth of the internet. What good is a clear text URL line User+PWD transmission if anyone or organization can catch and parse this?
Since when do spies like to get spied on

So my questions:
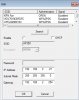
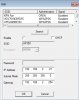
- Did anyone find a way to “hack” into the cam by
- TELNET and or
- SOFIA and or
- Conifg file (these mysterious JSON config files: after DL I unzipped it and can see all the nice files but can’t do anything with them: who can and how?) and or
- by some URL line commands and or
- ONVIF command? And or
- Home cooked / modded firmware
__To upload a valid SSL certificate (I managed to create my own but it looked like the upload ended in null device  , or to somehow enable the HTTPS and SSL SMPT email account access and to resolve the complete safety / privacy / eavesdropping issues?__
, or to somehow enable the HTTPS and SSL SMPT email account access and to resolve the complete safety / privacy / eavesdropping issues?__
What is exactly the purpose of these open ports: ??SOFIA?: 9527, ??: 8899, ??: 34567.So far I use mainly HTTP 80, RTSP 554, TELNET 23
May the 4th be with you.