You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
alastairstevenson
Staff member
What's the exact model of the device? Presumed a Hikvision NVR.Anybody knows what's going on?
What firmware are you loading? (link, presumed stock firmware)
What's the existing firmware version? (SADP)
It is a DVR DS-7204HQHI-K1/A. I've been using the recorder for several months, but recently I had a problem with it.
Suddenly stopped responding, even after power reset there is no buzzer sound. In the TTL terminal (UART) it stops at "Starting kernel". When trying to upload a new firmware, I get this error "cramfs.img checksum error".
Once I had the same recorder blocked and I uploaded the firmware to unlock it as described here. Now I can't upload the firmware.
Suddenly stopped responding, even after power reset there is no buzzer sound. In the TTL terminal (UART) it stops at "Starting kernel". When trying to upload a new firmware, I get this error "cramfs.img checksum error".
Once I had the same recorder blocked and I uploaded the firmware to unlock it as described here. Now I can't upload the firmware.
alastairstevenson
Staff member
I'm speculating that there may be a memory fault.
The file is being downloaded to RAM and then verified. The verification fails, suggesting the data has been corrupted.
The file is being downloaded to RAM and then verified. The verification fails, suggesting the data has been corrupted.
Howdy. Does anyone know how to reset password (ie. force re-activation) of the device on this board? The device model is DS-7316HUHI-K4
I've seen that some of them have switches, but this one does not. Perhaps it has a jumper somewhere, but there are so many candidates and no obvious one.
I was thinking perhaps the one next to the capacitors on the left hand side?


I've seen that some of them have switches, but this one does not. Perhaps it has a jumper somewhere, but there are so many candidates and no obvious one.
I was thinking perhaps the one next to the capacitors on the left hand side?


I'm speculating that there may be a memory fault.
The file is being downloaded to RAM and then verified. The verification fails, suggesting the data has been corrupted.
I see there is a command for memory test: mtestall.
Can I check the RAM with this command? If so, how to use it?
alastairstevenson
Staff member
I don't know, it's not a command I've used.I see there is a command for memory test: mtestall.
Can I check the RAM with this command? If so, how to use it?
Just try it and see what happens.
Hopefully if it needs parameters it will list them.
jason.online.111
n3wb
Thank you for writing this in such a detailed manner.
This helped me bring back to life an NVR NR32P8-8 box over the weekend.
It amazes me when people like you write these "how to" documents and I always wonder, how long it took to find the solution, how many hours of research and testing, countless.
I wish I could at least buy you a coffee or some chocolate.
Cheers!
This helped me bring back to life an NVR NR32P8-8 box over the weekend.
It amazes me when people like you write these "how to" documents and I always wonder, how long it took to find the solution, how many hours of research and testing, countless.
I wish I could at least buy you a coffee or some chocolate.
Cheers!
I've saved a lot of hardware over the years thanks to your posts.Well, that's a terrific post for a thread starter. Kudos for the level of detail, clarity and effort that's gone into it.
The thread could very well turn into a valuable reference source that many people could get some benefit from.
So, if I may, I'd like to maybe add a few more items that could be useful.
By the way - I do agree generally with your sentiments about Hikvision's practice of trying to punish those customers who have purchased on-line at much lower cost than if it had been via an 'authorised' source. That's one reason why I've been so keen to help out those whose cameras have 'bricked' when doing what should come naturally - a firmware update for bugfixes, security fixes and functionality.
Firstly - in terms of a lost password, the tftp update of nominally the same firmware that's installed is certainly one approach.
But I'd caution people trying this to somehow find out if their NVR is a China market model running 'hacked to English' firmware. This would generally be those NVRs with the -N model suffix as opposed to the -NI suffix.
An update with stock firmware for those models will likely result in a bricked NVR having the " !!! You device is illegal !!! !!! You bought in China !!! ....." 15-beep bootloop.
So be careful.
The serial console is a powerful way to access the internals of an embedded Linux device, and particularly so on Hikvision devices, when they have been designed with deliberate traps and blocks to stop people doing what they think they should be able to on the products that they have purchased.
Despite these obstacles, there are enough clever people around who have the inquisitiveness and ability to explore them and work round them, so in reality it's a fairly pointless tactic, given the power of internet search these days.
It's not hard to see that Hikvision do take note of any openly-published 'tweaks' and incorporate measures against them in new firmware releases.
So I was going to describe here a really simple way to gain very good access to Hikvision NVR internals - but find that I'm having second thoughts about doing so.
Whilst it may be that the firmware for the DS-76xxNI/E series has probably reached end-of-life, this trick works even better on later models where the firmware is still being worked on and where there is a r/w file system instead of the previous CRAMFS r/o file system.
hello, I have an axiom hub control unit, I don't understand what happened to the control unit, there are no functions despite having done a factory reset, I was wondering if it is possible to do this procedure also for the alarm control units by sending them the firmware again last thanks
I have attached a photo, I think this is the connector but I don't know where the connections go
I had done this procedure 2 times with 2 DVRs, one turbo and the other older, I think it can also be done for this control unit
I have attached a photo, I think this is the connector but I don't know where the connections go
I had done this procedure 2 times with 2 DVRs, one turbo and the other older, I think it can also be done for this control unit
Attachments
Last edited:
alastairstevenson
Staff member
My guess is that the tftp server IP address is not 192.0.0.128I tried but without success, putty does not send the firmware
Just use the normal IP address of the PC, and pick an unused address in the same range for the NVR to use. It's just temporary, it doesn't stick.
crisdolosa
n3wb
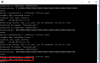
Hello, im trying to reload firmware onto my DVR, trying to remove password. but im having trouble updating using tftp as seen below
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMOFB
MLE
RBE
RESET TYPE : Power on reset
Calibration Progress : Done
SPL Nor Load!
SPL Nor flash boot!
RBE
U-Boot 2017.09-svn48627 (Jul 30 2020 - 09:39:36 +0800), Build: jenkins-Backend-BSP-CCI-1544
DRAM: 512 MiB
In: uart@0x18300000
Out: uart@0x18300000
Err: uart@0x18300000
Net: eth0: ethernet@1b900000
Chip-mode : sec-chip
Hit ctrl+u to stop autoboot: 0
HKVS $ update
HKVS $ setenv ';update'
Spi flash unprotecting...
Done! Unprotection status:[0x4204]=>[0x200].
### CRAMFS load complete: 3674608 bytes loaded to 0x82000000
the uImage support update_v3.
Verifying RSA ... OK
## Booting kernel from Legacy Image at 82000000 ...
Image Name: Linux-4.9.138
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 3674030 Bytes = 3.5 MiB
Load Address: 80008000
Entry Point: 80008000
Verifying Checksum ... OK
Loading Kernel Image ... OK
Starting kernel ...
Thu Jan 1 00:00:01 UTC 1970
mv: can't rename 'ubi*': No such file or directory
Starting udev: [ OK ]
waiting for net_link [10]...
waiting for net_link [9]...
waiting for net_link [8]...
waiting for net_link [7]...
waiting for net_link [6]...
waiting for net_link [5]...
waiting for net_link [4]...
-0-[ 10.225310] dwceqos 1b900000.ethernet eth0: Link is Up - 10Mbps/Half - flow control off
This program will download and upgrade software.
***
ftp server not exit[-111]!
recv failed,errno[-11]!
state machine action error[-110]
update_download error!
Press ENTER key to reboot
Thank you
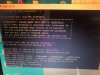
MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMOFB
MLE
RBE
RESET TYPE : Power on reset
Calibration Progress : Done
SPL Nor Load!
SPL Nor flash boot!
RBE
U-Boot 2017.09-svn48627 (Jul 30 2020 - 09:39:36 +0800), Build: jenkins-Backend-BSP-CCI-1544
DRAM: 512 MiB
In: uart@0x18300000
Out: uart@0x18300000
Err: uart@0x18300000
Net: eth0: ethernet@1b900000
Chip-mode : sec-chip
Hit ctrl+u to stop autoboot: 0
HKVS $ update
HKVS $ setenv ';update'
Spi flash unprotecting...
Done! Unprotection status:[0x4204]=>[0x200].
### CRAMFS load complete: 3674608 bytes loaded to 0x82000000
the uImage support update_v3.
Verifying RSA ... OK
## Booting kernel from Legacy Image at 82000000 ...
Image Name: Linux-4.9.138
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 3674030 Bytes = 3.5 MiB
Load Address: 80008000
Entry Point: 80008000
Verifying Checksum ... OK
Loading Kernel Image ... OK
Starting kernel ...
Thu Jan 1 00:00:01 UTC 1970
mv: can't rename 'ubi*': No such file or directory
Starting udev: [ OK ]
waiting for net_link [10]...
waiting for net_link [9]...
waiting for net_link [8]...
waiting for net_link [7]...
waiting for net_link [6]...
waiting for net_link [5]...
waiting for net_link [4]...
-0-[ 10.225310] dwceqos 1b900000.ethernet eth0: Link is Up - 10Mbps/Half - flow control off
This program will download and upgrade software.
***
- ATTENTION!! PLEASE READ THIS NOTICE CAREFULLY! *
- Don't reset machine,or anything that interrupt it. *
- The upgrade process must finish in 10 minutes! *
- If this program fails,machine might be unusable, *
- and you will need to reflash again. *
- If you find this too risky,power off machine now. *
ftp server not exit[-111]!
recv failed,errno[-11]!
state machine action error[-110]
update_download error!
Press ENTER key to reboot
Thank you
alastairstevenson
Staff member
What ftp server are you running and what is the IP address of the PC it is running on?ftp server not exit[-111]!
recv failed,errno[-11]!
Also your LAN connection between the DVR and the network the PC is on seems to have faults.
crisdolosa
n3wb
What ftp server are you running and what is the IP address of the PC it is running on?
Also your LAN connection between the DVR and the network the PC is on seems to have faults.
I'm using the TFTP server of hikvision with PC ip address of 192.0.0.128.
i can also ping the 192.0.0.64 while the script above is runnning. i don'tknow if i missed something.
it is not a nvr but it is a central axiom alarm, will the connection be correct? I can't find anywhere else that this has happened to anyone else.My guess is that the tftp server IP address is not 192.0.0.128
Just use the normal IP address of the PC, and pick an unused address in the same range for the NVR to use. It's just temporary, it doesn't stick.
the problem is that the control unit works but a user who manages everything has been set up which is not admin.
even doing a reset from the key doesn't change anything I can't understand stuff like this has never happened
I don't understand how to reset the control unit to the factory values, even by holding down the button it resets asking me for the admin password, but then once logged in I have many functions disabled such as adding sensors or the section for updating. I only view: you don't have permission
How is this possible if I'm logged in as administrator?
Last edited:
alastairstevenson
Staff member
?it is not a nvr but it is a central axiom alarm
Was this intended for a different thread?
how i don't understand??
Was this intended for a different thread?
sandu dumitru
n3wb
On a DS7216HQHI DVR, I'm trying to upgrade the firmware via serial. I press CTRL+U at startup, but the DVR loads normally and does not enter the upgrade procedure
What am I doing wrong? Thank you
What am I doing wrong? Thank you
alastairstevenson
Staff member
After bootup, does it echo the characters you type? If not, check your TX connection.
Press Control-U till it auto repeats then power on the DVR.
Press Control-U till it auto repeats then power on the DVR.